IoT vulnerabilities: How to identify and secure connected devices
All internet-enabled devices are at risk of being hacked into and exploited, but Internet of Things (IoT) devices tend to have weaker standards of security compared to the likes of computers and smartphones. As such, they can introduce gaps in your network security that aren’t always obvious.
This guide looks at common IoT vulnerabilities, including device-level and network-level weaknesses, and shows you practical ways to reduce the risks they create for your home network.
What are IoT vulnerabilities?
Internet of Things (IoT) vulnerabilities are inherent weaknesses in IoT devices like smart cameras, TVs, doorbells, speakers, thermostats, and wearables. These weaknesses can exist in the hardware, the software, or the way the device connects to your network.
Attackers can exploit these vulnerabilities to get into the device itself or gain access to the network it’s part of and move deeper into it. Once inside, they may steal data, take control of devices, or even pull those devices into IoT botnets, which are large groups of infected machines used to launch bigger cyberattacks.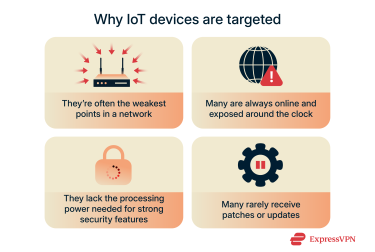
Most common IoT security risks
IoT security risks fall into two categories. Device-level risks come from flaws in the hardware, software, or default settings. Network-level risks come from the way IoT devices send data, connect to other systems, and interact with the wider network.
Device-level vulnerabilities
Default passwords and settings
Many IoT or Industrial Internet of Things (IIoT) devices ship with weak default or hardcoded passwords that are often short, simple, and relatively easy for attackers to crack. Once they get a device’s password, it becomes much easier for them to change settings, access features, or pull data from the device.
IoT devices also usually come with basic default settings designed to make setup quick. The problem is that these defaults often include insecure permissions or unnecessary features switched on, such as old services like Telnet for remote access. If they’re left unchanged, attackers can use those defaults to get into the device.
Outdated firmware and components
Many IoT devices use firmware and software components that rarely get updated, so they quickly fall behind on security fixes. Even when they exist, updates can be hard to apply. Some IoT devices have slow connections, limited storage, or clunky update systems, which means users may never install the patches even when they’re available.
Another issue is that many IoT devices use ready-made code, like open-source libraries or third-party components, to speed up development. Some of this code hasn’t been updated in years, and because it’s publicly available, attackers can study it, find weaknesses, and use those flaws to target any device that includes it.
Weak authentication
Even when a password isn’t the problem, many IoT devices rely on very basic authentication systems. Some don’t limit how many login attempts someone can make, some expose control panels or services that don’t fully verify the user, and others use outdated methods for confirming a device or app is allowed to connect.
Even if the device itself doesn’t collect or contain any sensitive data, it can still act as a doorway into the rest of the network. Once attackers break into one weak device, they may be able to reach others on the same network.
Lack of physical hardening
Some IoT devices sit in places that anyone can reach, like smart doorbells, outdoor cameras, and sensors. If a device is easy to reach and lacks physical protections like sealed casings, hidden ports, or tamper alerts, it makes it easy for an attacker to tamper with it directly.
They might open the casing, plug into exposed or unused ports, remove components, or read unprotected storage that holds things like Wi-Fi details. Some devices even leave debug ports or removable memory cards accessible, which makes it easier for an attacker to install malware or pull data.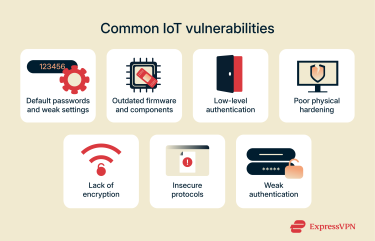
Network-level vulnerabilities
Lack of encryption
Many IoT devices either don’t encrypt the data they send and receive, or they use weak, outdated encryption, a security process that turns readable information into scrambled text that can’t be understood without the right key. That means if someone penetrates the network or gains access to the device, they could intercept and read that data with ease.
While this may not be the biggest problem on IoT devices that don’t collect or store much or any sensitive data, it’s much more of an issue on those that are capable of collecting and transmitting large amounts of personal information, like smart cameras and home hubs.
Insecure communication protocols (e.g., MQTT, CoAP)
Many IoT devices use communication protocols like Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP). These protocols are designed to run on low-power hardware, making them well-suited for IoT devices that don’t have much processing power.
However, they don’t include strong security features by default, and when manufacturers don’t add proper protections, like encryption or authentication, attackers can intercept or tamper with the device’s traffic more easily.
Weak network access
A large percentage of IoT devices have insecure network setups that make them too easy to reach from inside or outside the network. For example, some devices leave unnecessary ports open, expose web interfaces that anyone on the network can access, or allow remote connections without proper checks.
Some even accept traffic from the internet when they were never meant to be accessed directly at all. These gaps give attackers more opportunities to connect to the device and attempt to break in.
Real-world examples of IoT attacks
There have been numerous high-profile examples of IoT attacks, especially in recent years as IoT devices become more prevalent in homes and businesses worldwide.
The Mirai botnet
The 2016 Mirai botnet was one of the largest IoT attacks ever to occur. The worm-like family of malware behind it was able to compromise large numbers of internet-connected products with weak security protections, creating a vast network of hijacked devices known as a botnet.
The botnet was then used for distributed denial-of-service (DDoS) attacks, initially used to take down rival Minecraft servers but quickly escalating to high-profile targets, most notably security blogger Brian Krebs’s site in September 2016 and the DNS provider Dyn on October 21, 2016. This attack disrupted access to many major websites, such as Twitter, Netflix, Reddit, Spotify, and The New York Times.
Mirai demonstrated how weak IoT security and seemingly simple devices could be used for large-scale cyberattacks with far-reaching consequences. In the wake of this attack, more companies started to take IoT security seriously.
Notable IoT device breaches
There have been numerous other reports and allegations of IoT devices being vulnerable to use for malicious purposes, including smart cameras, security systems, baby monitors, and home hubs.
Smart camera exploits
- Hikvision camera flaws: In 2021, reports emerged of a critical vulnerability in several Hikvision IP cameras, which could allow attackers unauthorized access to administrative functions, until Hikvision released a firmware fix.
- Verkada camera breaches: A 2021 breach affecting up to 150,000 cloud-connected cameras enabled cybercriminals to access video or image data for 97 Verkada customers. Verkada took swift steps to secure customer data and reinforce system protections.
- TRENDnet baby monitor exploits: In 2012, a privacy vulnerability was reported that allegedly exposed video feeds from consumer webcams. The company later issued firmware updates to close the vulnerability and agreed to improve its security practices under a Federal Trade Commission (FTC) settlement.
Smart home hub hacks
While there haven’t been any high-profile cases involving smart hub homes, cybersecurity researchers have reported potential flaws in these devices in the past:
- Amazon Alexa devices: In 2020, researchers reported that a weakness in Amazon’s Alexa code could have allowed attackers to gain access to the device and user data, but no reports emerged of the exploit being used, and Amazon immediately took action to rectify the issue.
- Google Home and Nest: In 2021, cybersecurity expert Matt Kunze reported a bug in the code of Google Home and Nest Hub devices that could, theoretically, allow attackers to access and control these devices remotely. Once Google became aware of this vulnerability, it took necessary steps to address it.
How to secure your IoT devices
Manufacturers have a big responsibility to secure their IoT devices prior to release and post-release through the likes of secure passwords and protocols, along with patches to fix any identified vulnerabilities. However, users can also take steps to make their IoT devices as secure as possible.
Device security best practices
Good device habits go a long way toward keeping your network safe. When you get an IoT device, one of the most important steps is to turn off features you don’t use, such as remote access or location tracking, because unnecessary functions can create extra openings for attackers.
You should also make sure your Wi-Fi is using the strongest security option your router supports, like Wi-Fi Protected Access 3 (WPA3) if available, and watch for any unusual behavior on your network or any devices that seem to run slower than expected. Finally, when possible, choose IoT products from reputable brands that provide clear support and regular updates.
Strong password policies
Whenever possible, you should change the default passwords on your IoT devices. Weak or default credentials make it easy for attackers to break in, since many IoT passwords are publicly known or easy to guess. Switching to strong, unique passwords for each device solves most of that risk. A good password manager can help you generate secure passwords and keep track of them without having to remember each one.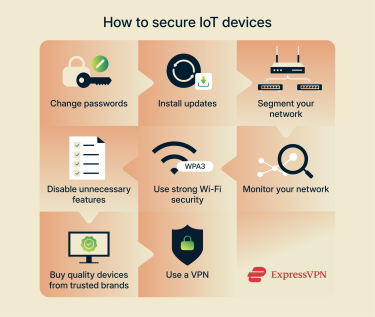
Network segmentation
Network segmentation is the process of splitting your network into smaller, isolated subnetworks. This means that even if hackers gain access to an IoT device, they’re contained within that segment and can’t easily move on to more important devices like computers or phones. Here are some practical ways to segment a network:
- Guest networks: Most home routers let you create a separate “guest” Wi-Fi network. It’s a quick, simple way to put your IoT devices on their own network without letting them interact with your main devices.
- Secondary routers: Using a second router physically separates your IoT devices from everything else. This creates a completely separate network, which gives you stronger isolation but requires extra hardware.
- Virtual local area networks (VLANs): Some advanced routers let you create virtual subnetworks inside the same device. It’s similar to a guest network but gives you much finer control over which devices or groups can talk to each other.
Firmware updates and patch management for IoT
Updates are one of the most effective ways to keep IoT devices secure. Some devices get full firmware upgrades, others receive smaller patches that fix specific vulnerabilities, and a few may never get updates at all. Whenever a new version is released, install it as soon as you can, since these updates often address security flaws that attackers actively look for.
Depending on the device, updates may not install automatically, so it’s worth checking the manufacturer’s app or website every so often to see if new releases are available.
Using a VPN to encrypt IoT traffic
A virtual private network (VPN) is another useful tool for improving network security when using IoT devices. It works by forming a secure, encrypted tunnel between your devices and secure VPN servers, which helps solve the lack of encryption issue that many IoT devices suffer from.
Many VPNs won’t actually work on IoT devices individually, since these devices don’t have the built-in support in place to run VPN apps and protocols. But you can still secure your IoT connections by installing a VPN on your router; for example, the Aircove router has a built‑in VPN that protects all devices connected to the network. (Note that you need an active ExpressVPN subscription to use the VPN.)
Legal and regulatory landscape
As IoT devices become more common and their weaknesses create bigger risks for users, governments around the world are exploring new ways to address these issues and mitigate the risks they pose.
The IoT Cybersecurity Improvement Act of 2020
The U.S. government enacted the IoT Cybersecurity Improvement Act of 2020, a federal law that creates a clear framework for secure IoT design and deployment. It sets out the security standards and features manufacturers must follow when building IoT devices intended for use by federal agencies.
While this act doesn’t apply to consumer IoT devices, it does provide some knock-on benefits for everyday consumers and public safety. That’s because many manufacturers follow the same standards across their product lines, which helps make everyday IoT devices safer overall.
GDPR and IoT compliance
The General Data Protection Regulation (GDPR) is an EU regulation designed to protect the data and privacy of EU residents. It sets out strict rules for how organizations should gather, store, and process people’s personal data, and it applies to personal data collected or processed by IoT devices across the EU.
IoT device manufacturers intending to sell their devices in Europe therefore must abide by GDPR guidelines. They need to obtain user consent before collecting any data, make sure customers understand how that data will be used, and provide them with the ability to access, correct, or request deletion of their information. This encourages better data practices and, over time, can make IoT devices safer for users.
FAQ: Common questions about IoT vulnerabilities
What is an IoT vulnerability?
An Internet of Things (IoT) vulnerability is a weakness in an IoT device, like a smart speaker, that can be exploited. Examples of IoT vulnerabilities include weak passwords, outdated firmware, or an absence of encryption when storing or transmitting data. These vulnerabilities may allow attackers to gain access to devices, networks, and sensitive data.
What are the most common vulnerable IoT devices?
Routers and smart home devices, including smart TVs, speakers, security cameras, and appliances, tend to suffer the most from Internet of Things (IoT) vulnerabilities. Common issues impacting these devices include weak or default passwords, insecure network protocols, and poor authentication practices.
How can I test my IoT device for security flaws?
You can look up your Internet of Things (IoT) device online to quickly find out about any known vulnerabilities and security recommendations, as well as explore its settings and features to look for common weaknesses, like default passwords and outdated firmware. You can also use network monitoring tools to keep track of traffic flowing to and from your IoT device to potentially spot warning signs, such as unencrypted data.
What is the best way to secure my home network for IoT?
The best way to secure your network for Internet of Things (IoT) devices is to take a holistic approach to network security, securing both your router and your various IoT devices, one by one. Opt for the strongest available security protocols, like Wi-Fi Protected Access 3 (WPA3) on your router, and change default IoT passwords to more secure, complex alternatives. Also ensure you install any available firmware updates at the earliest opportunity and disable IoT features you don’t use, like smart TV voice controls.
Is IoT data protected under GDPR?
Yes, the General Data Protection Regulation (GDPR) applies to personal data stored, collected, or transmitted between Internet of Things (IoT) devices. Businesses that make and manage these devices have to ensure that their data collection processes are compliant. IoT device users, meanwhile, have to give consent for any and all data collection and have the right to request that their IoT data be deleted.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN