What is the International Data Encryption Algorithm (IDEA) in cryptography?
Encryption algorithms secure most of what we do online, from sending messages to storing data. As technology evolves, some algorithms remain in use while others become historical references for understanding modern encryption.
The International Data Encryption Algorithm (IDEA) is best known today as a legacy cipher that may still appear in older systems for backward compatibility. This article explains what IDEA is, how it works, and how it compares to modern encryption standards.
What is the IDEA algorithm?
IDEA is a symmetric-key block cipher used for data encryption. Unlike asymmetric encryption, which uses separate keys for encryption and decryption, IDEA uses one secret key for both operations.
Xuejia Lai and James Massey developed IDEA in the early 1990s, building on an earlier design called Proposed Encryption Standard (PES).
IDEA's design is based on applying multiple transformations to data during encryption. The algorithm processes each block through eight rounds, each using distinct mathematical operations and subkeys. This approach helps to reduce detectable patterns in the ciphertext.
How does IDEA encryption work?
IDEA uses the Lai-Massey scheme (a block cipher structure) to encrypt data, whether it’s stored on a device or sent across a network, depending on the protocol and mode used.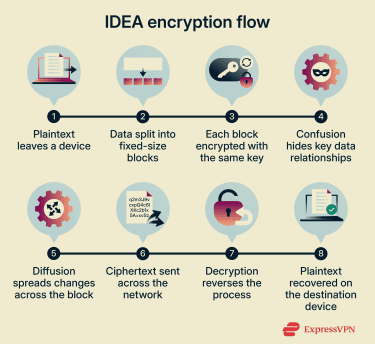
The algorithm is designed around two key goals often discussed in encryption design: confusion and diffusion. To understand why they matter, it helps to think about what encryption is actually trying to prevent.
The first threat is pattern recognition. If small changes in a message produced small, predictable changes in the encrypted output, an attacker could compare encrypted versions of similar messages and start piecing together what changed.
Diffusion helps counter this by spreading the effect of a small change in the original message across the entire encrypted output. For example, if a message reads “Transfer $100” and it changes to “Transfer $900," only one character has changed.
But because of diffusion, that single change doesn't produce a small, localized difference in the ciphertext. Instead, it alters the output in broad, unpredictable ways, so the two encrypted messages look completely unrelated.
The second threat is key inference. Even if an attacker can't read the message, they might try to work backward from the encrypted output to figure out the secret key. If the relationship between the key and the ciphertext were transparent or consistent, enough encrypted samples could eventually reveal it.
Confusion helps by making the way the key shapes the encrypted output mathematically complex, so there’s no clear, traceable connection between key material and ciphertext.
In the same example, even if an attacker knew the message changed from 100 to 900 and could see both ciphertexts, they still couldn't identify which parts of the output correspond to the key or how it was applied.
Together, these properties make it much harder to detect useful structure in the ciphertext, even when an attacker understands how the algorithm works.
Block size and key length
IDEA encrypts data in 64-bit blocks (8 bytes at a time), similar to Blowfish encryption. A single character in plain text usually takes up one byte, so a 64-bit block can hold about 8 characters, although the exact number of characters depends on the text encoding.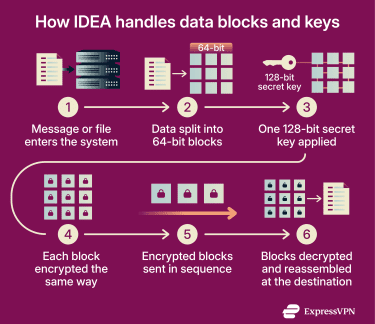
IDEA uses a 128-bit secret key to control how the data is encrypted and decrypted. The key acts as a shared secret between the sender and the receiver. Both parties must possess the same key to decrypt the original message.
The size of the key affects the number of possible key combinations. A 128-bit key allows for an extremely large number of possibilities, making brute-force attacks impractical.
When encrypting data longer than one block, IDEA is applied repeatedly to successive blocks, typically using a mode of operation and, in many cases, an initialization vector (IV) / number used once (nonce). The same master key is used for the message, while internal round keys are derived from it.
Round structure and operations
Each block of data passes through eight rounds, followed by a final transformation. In each round, IDEA splits the 64-bit block into smaller parts, mixes them through a series of steps, and recombines them before moving to the next round.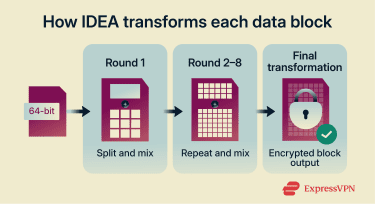 During these rounds, IDEA applies several types of mathematical operations. These include bitwise exclusive OR (XOR), addition modulo 216 (65536), and multiplication modulo 216+1 (65537).
During these rounds, IDEA applies several types of mathematical operations. These include bitwise exclusive OR (XOR), addition modulo 216 (65536), and multiplication modulo 216+1 (65537).
Each operation transforms data in a different way. XOR works at the bit level, changing individual bits based on the key. However, addition and multiplication treat 16-bit chunks as numbers and combine them mathematically. For example, instead of just changing a single bit, the algorithm might add two 16-bit modulo 216, producing a result that differs across many bits, not just one.
Key schedule
IDEA expands the 128-bit master key into many smaller subkeys rather than using the entire key in each round. Using different subkeys across rounds creates more complex transformations, thereby strengthening the encryption.
Each round of encryption uses a specific group of subkeys, ensuring the master key influences data throughout the entire encryption process, not just at the beginning.
When the sender and receiver share the same secret key, IDEA generates the same subkeys in the same order on both sides. This keeps encryption and decryption in sync without sharing extra information.
How IDEA decrypts data
Once data reaches its destination, IDEA decrypts it. It uses the same round structure and operations to transform the ciphertext back into its original form.
The difference is that it applies the subkeys in reverse order to undo the encryption. Because both sides start with the same secret key, they can generate the same set of subkeys and reverse the transformation step by step. This symmetry is a key feature of IDEA’s design.
Security of the IDEA algorithm
IDEA was well regarded when first introduced, and cryptography researchers have studied it closely for many years. While researchers have identified certain theoretical weaknesses, no widely accepted practical break of IDEA under real-world conditions is known. For a long time, IDEA was a respected encryption algorithm used in early end-to-end encryption (E2EE) systems.
However, encryption standards have evolved. To meet modern requirements, an algorithm must perform reliably at scale, integrate with modern protocols, and comply with current security guidance.
Practical limitation
A key limitation of IDEA is its 64-bit block size. Because the algorithm encrypts data in fixed-size blocks, the number of possible block outputs is large but finite.
When systems encrypt large amounts of data or maintain encrypted connections for extended periods, the chance of block collisions (repeats) increases. This is sometimes described as a birthday boud effect, named after the birthday paradox: in any group of 23 people, there’s a greater than 50% chance that two share a birthday.
What this reveals depends on the mode of operation, but in high-volume or long-lived sessions, such as older Transport Layer Security (TLS) configurations using 64-bit block ciphers, collisions can leak information or enable practical attacks.
Because modern systems often encrypt gigabytes of traffic in a single session, these risks can appear much sooner with a 64-bit block size than with 128-bit blocks.
Researchers have also identified specific weak-key classes and related-key attack models for IDEA. These results generally assume conditions that don’t usually hold in practice, such as an attacker being able to influence key generation or obtain encryptions under multiple keys with known relationships.
Together, these limitations mean IDEA is best treated as a legacy cipher. Current security practice for protocols such as TLS is to avoid 64-bit block ciphers and prefer modern standards such as Advanced Encryption Standard (AES).
IDEA vs. AES: How do they compare?
IDEA reflects early 1990s design priorities, while AES was later standardized and widely adopted, with strong support on modern hardware and in current protocols.
| IDEA | AES | |
| Block size | 64 bits | 128 bits |
| Key sizes | 128 bits | 128, 192, or 256 bits |
| Security | Strong core design; 64-bit block-size limits at high volumes | Widely analyzed; recommended for modern deployments |
| Performance | Efficient in software; limited widespread hardware acceleration | Often hardware-accelerated on modern CPUs |
| Usage | Rare, mostly legacy compatibility | Standard across modern systems |
In practice, AES is the default choice for new deployments because it’s widely standardized, performs well on modern hardware, and avoids the scaling limits of 64-bit block ciphers in high-volume settings, such as virtual private network (VPN) traffic and encrypted storage.
FAQ: Common questions about the IDEA algorithm
What are the main types of cryptographic algorithms?
Cryptographic algorithms generally fall into three main categories:
- Symmetric-key algorithms: Use the same secret key for both encryption and decryption. For example, the International Data Encryption Algorithm (IDEA) and the Advanced Encryption Standard (AES).
- Asymmetric-key algorithms: Use a pair of keys (public and private) for tasks like encryption, digital signatures, and key exchange.
- Hash functions: Convert data into a (typically) fixed-length digest used for integrity checks and other purposes, and are designed to be one-way (computationally infeasible to reverse).
How many rounds are used in IDEA?
The International Data Encryption Algorithm (IDEA) uses eight full encryption rounds, followed by a final transformation step. Each round applies the same overall structure but uses different subkeys derived from the main secret key.
What are the key advantages of IDEA encryption?
The International Data Encryption Algorithm (IDEA) is known for its careful, well-studied design. It combines multiple mathematical operations and repeated rounds to change data during encryption. Over the years, researchers have analyzed it extensively, and no widely accepted practical break is known, even though academic attacks on reduced-round and full-round variants have been published under specific models and assumptions.
Is IDEA encryption still relevant today?
The International Data Encryption Algorithm (IDEA) is no longer widely used in modern systems. Its 64-bit block size doesn’t align with today’s encryption needs, especially for high-volume or long-lived encrypted connections. Modern standards and protocols generally favor newer algorithms, such as the Advanced Encryption Standard (AES), which are better suited to current security requirements and modern hardware.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN