What is a BEC attack, and how do you protect your business?

A business email compromise (BEC) attack exploits trusted business email accounts used for payments and sensitive communications, tricking employees into sending money or confidential information to attackers. These attacks succeed by blending into everyday business processes, making fraudulent requests difficult to distinguish from legitimate ones.
Understanding how BEC attacks work and recognizing their warning signs can reduce the risk of financial loss and data exposure. This guide explains the different forms a BEC attack can take and how organizations detect, prevent, and respond to BEC threats before they escalate.
What is a business email compromise (BEC) attack?
A BEC attack is a cybercrime in which attackers misuse email communication to trick organizations into sending money or sensitive information. These attacks rely significantly on impersonation through spoofed email addresses, trust, and social manipulation.
Attackers typically pose as someone within the organization or a trusted partner, sending messages that appear to be legitimate workplace requests. Because these emails blend into everyday workflows, they’re often harder to detect than more generic scams.
What makes BEC particularly dangerous is its precision. Attackers study how an organization operates, identify key decision-makers, and time their messages to align with real business activity. Without clear verification processes, these requests can appear legitimate and slip through unnoticed.
The FBI describes BEC as one of the most financially damaging forms of cybercrime, with losses exceeding $55 billion between 2013 and 2023.
BEC vs. phishing: Key differences
Phishing refers to a social-engineering technique used to deceive recipients into revealing information or taking harmful actions. It can be broad and automated, but it can also be highly targeted, as in spear-phishing or whaling attacks.
BEC is a specific type of fraud that often relies on phishing techniques. In BEC attacks, criminals impersonate trusted individuals or compromise real email accounts to manipulate business processes (such as payments, invoices, or data requests) rather than delivering malware or directing victims to malicious links.
While many phishing attacks aim to steal credentials or spread malware, BEC attacks typically focus on financial or operational fraud and often involve emails that contain no links or attachments at all. For this reason, BEC is better understood as a phishing-enabled fraud scenario, not a separate alternative to phishing.
| Phishing (general) | BEC | |
| Category | Social-engineering method | Fraud scenario |
| Typical goal | Credentials, malware, data | Money or sensitive business info |
| Targeting | Broad or targeted | Highly targeted |
| Links/attachments | Often present | Often absent |
How do BEC attacks work?
A typical BEC attack begins long before any fraudulent message is sent. The attacker first researches the organization, identifying employees involved in finance, HR, or executive decision-making, along with vendors, clients, and payment workflows. Publicly available information, such as LinkedIn profiles, press releases, or leaked invoices, is often enough to understand who approves payments, who requests them, and how money normally moves inside the business.
Once the attacker has sufficient context, they seek initial access. This is often achieved by phishing for email credentials, using reused or previously breached passwords, or exploiting gaps in email security or multi-factor authentication (MFA). While phishing may be involved at this stage, it functions as the entry method rather than the attack itself.
With access secured, the attacker either takes control of a legitimate email account or impersonates a trusted sender using a look-alike domain. If it’s a legitimate account, attackers often create secret email rules inside the compromised account to obscure their activity from the real account owner. These rules automatically delete, forward, or move certain messages out of the inbox without the user realizing it. For example, replies that question a payment request, messages mentioning invoices or wire transfers, or even security alerts about new logins may be silently redirected or removed. As a result, the real account owner never sees warning signs that something is wrong, allowing the attacker to monitor conversations, respond in their place, and continue the fraud for days or even weeks without detection.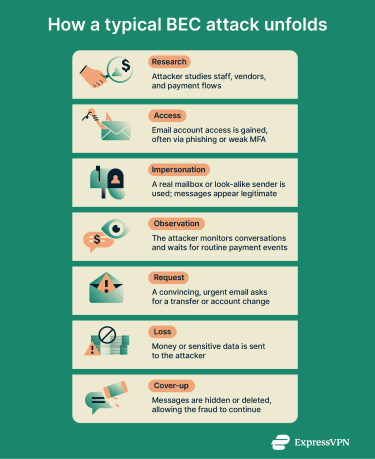
Rather than acting immediately, the attacker often spends time observing email traffic. They read real conversations, learn how employees write, and study approval patterns and timing. Many attackers wait for specific triggers, such as invoice cycles, payroll deadlines, or corporate transactions, before making their move. This patience is a defining characteristic of BEC attacks, which are typically slow and deliberate rather than opportunistic.
When the timing is right, the attacker sends a carefully crafted message. These emails reference real people, ongoing transactions, or familiar processes, and often create a sense of urgency or authority by invoking confidentiality or executive approval. Unlike many phishing emails, BEC messages usually contain no links or attachments. Instead, they request actions such as wiring funds, changing invoice payment details, updating bank information, or sharing sensitive documents.
If the recipient complies, money may be transferred to accounts controlled by the attacker, or sensitive business data may be disclosed. Stolen funds are often quickly moved through multiple accounts to make recovery more difficult.
After the fraud succeeds, the attacker may take steps to cover their tracks. This can include deleting sent emails, maintaining inbox rules to suppress warnings, or continuing to exploit access for additional fraud. In some cases, BEC incidents go unnoticed for weeks or even months before the organization realizes something is wrong.
Email impersonation and spoofing tactics
Impersonation plays a central role in many BEC attacks. Attackers use a combination of methods to make fraudulent messages appear to come from trusted individuals or known organizations.
One common approach is email spoofing. In this scheme, attackers display the name of a senior executive as the apparent sender, while the underlying email address originates from an external service controlled by the attacker, such as a free webmail provider. If the receiving system lacks proper email authentication checks, the message may still be delivered and appear trustworthy to the recipient.
In other cases, attackers may gain access to real email accounts that have been compromised through reused passwords, previously exposed credentials, or weak account security. They can then use these email accounts to send fraudulent requests within an existing conversation.
These tactics are effective because people tend to trust messages that match familiar communication patterns. When requests resemble routine correspondence and verification steps are unclear or inconsistent, impersonation attempts can go unnoticed.
Common social engineering techniques
Social engineering is central to most BEC attacks. Common techniques attackers use in emails to influence decision-making include:
- Authority abuse: Attackers pose as CEOs, finance directors, or senior managers, exploiting employees’ tendency to comply with requests from senior leadership.
- Familiarity building: Messages may reference real projects, recent meetings, or internal terminology. In some cases, attackers exchange harmless emails first to establish trust before making a fraudulent request.
- Believable pretexts: Attackers create plausible explanations for unusual requests, such as working remotely, having limited system access, or temporary email issues.
- Emotional pressure: Messages may appeal to loyalty or helpfulness or suggest that delays could reflect poorly on the recipient. Urgency is often framed as a test of reliability rather than an explicit threat.
Targeted roles in an organization
BEC attackers often focus on roles that can move money, approve changes, or pass requests along without raising suspicion. Some of the most commonly targeted teams include:
- Finance and accounting teams: These teams process invoices, payroll, and wire transfers. Attackers target these roles because payment requests are routine, making fraudulent invoices or urgent transfer approvals easier to disguise, especially during busy periods.
- Executive assistants and administrative staff: These roles often manage executive inboxes, schedules, and communications and may have authority to initiate payments or relay instructions.
- HR teams: Attackers may impersonate employees requesting changes to direct deposit information or ask for sensitive documents such as W-2 forms. These attacks are often timed around onboarding, when HR teams are interacting with new hires they may not yet know well.
- Procurement and vendor management teams: Since these teams regularly communicate with external suppliers, fraudulent requests can be harder to spot at a glance.
Types of BEC attacks
BEC attacks can take several forms, depending on the attacker’s goal and the role being impersonated. Here are a few common types.
CEO fraud (executive impersonation)
CEO fraud involves attackers impersonating senior executives, such as CEOs, CFOs, or managing directors. In these cases, the attackers craft messages typically directed at employees who handle payments, approvals, or sensitive operational tasks.
Because executive requests are typically treated as high priority, recipients may feel pressured to act quickly without verification. CEO fraud is especially effective in organizations where decision-making is centralized or urgent requests are common.
Timing plays a significant role in CEO fraud. Attackers often strike when the real executive is hard to reach, making it seem reasonable that the request is coming by email.
Vendor or invoice scams
Vendor and invoice scams take advantage of the routine nature of payment processing in most organizations. Attackers pose as trusted suppliers or service providers and try to redirect payments to accounts they control.
A common tactic involves an email that appears to come from a known vendor, claiming their banking details have changed. The message may reference real invoices or active projects and offer a plausible explanation, such as a system update or bank change.
In other cases, attackers modify invoices themselves. They may intercept vendor communications, then send nearly identical invoices with altered payment instructions timed to match expected payment dates.
The impact often goes beyond a single lost payment. Legitimate vendors may remain unpaid, relationships might be damaged, and multiple transactions may be redirected before the scam is discovered, making recovery difficult and costly.
Employee data theft
Some BEC attacks focus on stealing employee data, which can later be used for identity theft, tax fraud, or sold online. These attacks typically target HR teams, payroll staff, IT, and executives with access to sensitive employee records.
A common example is the W-2 scam. Attackers impersonate a senior executive and request copies of employee tax forms for “review” or “accounting purposes.” If the request is treated as legitimate, HR teams may inadvertently disclose names, addresses, Social Security numbers, and income details for large portions of the workforce.
Another frequent tactic is payroll diversion. In these cases, attackers impersonate employees and request changes to direct deposit information, causing paychecks to be redirected to accounts under the attacker’s control. These requests often coincide with onboarding or payroll processing cycles, when such changes are part of normal operations.
Legal or HR impersonation attacks
Legal or HR impersonation attacks exploit the perceived sensitivity, confidentiality, and time-critical nature of legal and HR matters. Because these topics are often treated as restricted or urgent, recipients may be less likely to verify requests with colleagues, increasing the risk that sensitive information is shared or actions are taken without proper confirmation.
In legal-themed impersonation scams, attackers pose as external attorneys or in-house counsel and claim to be handling urgent matters such as lawsuits, acquisitions, or regulatory issues. Requests may involve payments related to retainers or settlements, relying on the expectation that legal work often involves tight deadlines and limited internal disclosure.
In HR-focused impersonation attacks, messages may appear to come from HR leadership or related service providers and reference employee data, internal processes, or hiring activities. These requests can involve confidential employee information, payments, or participation in internal-looking surveys that lead to fraudulent outcomes.
Warning signs of a BEC attack
While BEC attacks are often difficult to detect, they may still show subtle warning signs. Identifying these indicators can help reduce the risk of financial loss or data exposure.
Here are some warning signs you should watch out for:
Pressure to bypass standard procedures
BEC emails often push recipients to skip or override normal approval processes. While urgency is relatively common in everyday work, these messages go a step further by framing routine checks as obstacles that must be avoided.
Attackers may claim that approval steps take too long, that key signatories are unavailable, or that the request is too sensitive to involve others. They often reference executives who are traveling, in meetings, or unreachable, and present the situation as an exception that requires immediate action.
This pressure to work “outside the usual process” is a key warning sign. When an email asks you to bypass established controls, it’s worth pausing and confirming the request through a separate communication channel before taking action.
Unusual payment instructions or account changes
Requests that involve changes to payment details, new bank accounts, or altered wire instructions should be treated with caution. Legitimate organizations rarely change financial information without advance notice and proper documentation. Even if the request appears to come from a trusted sender, deviations from normal payment processes can signal an attempted BEC attack.
You should be especially careful when payments are suddenly directed to foreign accounts. While international payments are common, an unexpected switch, particularly for a vendor you’ve always paid domestically, needs verification.
Another common warning sign is last-minute changes to payment instructions. In many BEC schemes, fraudulent messages appear shortly before a scheduled payment and introduce “updated” banking details. Changes that occur close to a payment date can be a strong indicator of attempted impersonation, particularly when they bypass established verification processes.
Requests for confidential data
Unexpected requests for sensitive information are another common sign of BEC scams. Most organizations have clear processes for sharing confidential data, so emails that bypass those channels or arrive without warning should be treated with caution.
Broad requests should be especially concerning. Messages asking for entire datasets, such as all employee W-2s, full customer lists, or complete financial records, go well beyond what legitimate business tasks usually require. Scammers often try to collect as much data as possible in a single request.
Attackers sometimes lean on authority to push these requests through. They may claim the data is needed by the CEO, an auditor, or a regulator, hoping employees will comply without questioning the request.
Another red flag is being asked to send sensitive data to a personal email address. Claims about email outages, remote work, or limited access are common excuses, but confidential information should stay within approved company systems.
Requests that discourage verification or insist on secrecy are particularly risky. If an email urges you not to confirm the request or warns against involving others, that’s a strong signal that something is wrong.
Inconsistencies in email headers or domains
Subtle inconsistencies in sender information can reveal a BEC attempt, especially when the message involves money or sensitive data. Taking a moment to check who an email actually came from can stop a scam before it goes any further.
One common red flag is a mismatched display name. An email might show a trusted name, like a CEO or manager, in the “From” field, but the underlying email address belongs to a different or unfamiliar domain. Many email apps hide this detail by default, which is why attackers rely on recipients not expanding the sender information.
Look-alike domains are another giveaway. These use small changes, such as extra words, swapped characters, or different domain extensions, to mimic legitimate addresses. For example, instead of accounts@acme.com, an attacker might use a look-alike such as accounts@acmme.com (extra characters), accounts@acme-payments.com (extra word), or accounts@acme.co (different domain extension).
Emails that claim to be from business contacts but use free email services such as Gmail or Outlook should also raise questions. While there are exceptions, internal staff and established vendors usually communicate from company domains.
Other subtle clues include missing or inconsistent email signatures or a tone and writing style that doesn’t match how the person usually communicates. Any combination of these signs is a good reason to pause and confirm the request through a trusted channel.
What to do if you suspect a BEC attack
Responding to a suspected BEC attack quickly and methodically can limit the damage. The priority should be to stop further interaction and involve the appropriate internal and external parties.
Immediate steps to take
- Preserve the evidence: Don’t delete the email or reply to it. Save the original message and take screenshots that show the sender's details, headers, and any attachments. Write down what happened while it’s still fresh, including a timeline of when the email arrived and what raised concern.
- Notify your IT or security team right away: Many organizations have a dedicated channel for reporting suspicious emails. The sooner they know, the faster they can investigate, block attacker domains, warn other employees, or contain a wider attack.
- Verify the request using a trusted, separate channel: If the email claims to be from an executive, call them using a number from your company directory. If it involves a vendor, contact them using known contact details, not anything provided in the email.
- If you’ve already acted on a fraudulent request, escalate immediately: Contact the relevant bank as soon as possible, and notify IT if any data was shared or links were clicked. Acting quickly gives your organization the best chance to limit damage.
Reporting to authorities and law enforcement
Reporting a suspected BEC attack helps authorities track criminal networks, spot patterns across cases, and improve the chances of recovering stolen funds. Reports may also be required for insurance claims, legal action, or regulatory compliance.
In the U.S., organizations may file a complaint with the FBI’s Internet Crime Complaint Center (IC3) at ic3.gov. Include a clear timeline, copies of the fraudulent emails, and any payment or account details.
If money was sent, contact your local FBI field office as well. FBI teams that handle BEC cases can sometimes work with banks to trace or freeze transfers, but timing is critical.
You should also report the incident to your local police department. This creates an official record that banks, insurers, or auditors may require, as well as a public record that can support legal proceedings or regulatory filings.
If bank accounts or wire transfers were involved, notify your financial institution immediately and ask to speak with their fraud team. Banks have established processes for BEC cases and can act quickly to limit losses.
For cases involving identity theft or employee data exposure, reporting to the Federal Trade Commission (FTC) through reportfraud.ftc.gov can help affected individuals access recovery resources.
Organizations in regulated industries should also check whether the incident triggers mandatory reporting to regulators. Legal counsel can help confirm what’s required based on the type of data or systems involved.
Finally, keep records of every report you file, including case numbers and contacts. These details are useful if new information emerges or follow-up is needed later.
Recovery and communication protocols
After the immediate risk is addressed, organizations should focus on recovery and internal communication. The organization should:
- Conduct a clear internal review: Reconstruct what happened, how the attacker succeeded, and which controls failed. Look at email logs, account activity, and approval workflows, and bring in security or forensic specialists for serious cases.
- Take immediate steps to close uncovered gaps: This might include resetting passwords, blocking malicious domains, tightening payment approvals, or improving email filtering.
- Communicate early and clearly with affected parties: This helps prevent confusion and reduces the risk of follow-up attacks. In some cases, organizations may also need to notify external partners or clients, depending on the nature of the incident and regulatory obligations.
- Review the incident response plan once the dust settles: Identify what worked, what slowed the response, and where responsibilities or communication broke down. Update playbooks so the next response is faster and more coordinated.
- Support employees involved in the incident: BEC attacks are designed to trick people, and blame-based responses discourage future reporting. Focus on learning, awareness, and reinforcing safe behaviors.
- Stay alert for follow-up attacks: Organizations that have been targeted once are often targeted again. Maintain heightened monitoring for a period before gradually returning to normal operations, this time with stronger controls in place.
How to prevent a BEC attack
Preventing a BEC attack requires a combination of technical controls, clear internal processes, and employee awareness. Since these attacks rely heavily on social engineering, no single solution can stop them on its own. The measures below, when implemented together, help limit both the likelihood and the impact of BEC attacks.
Enable multi-factor authentication
MFA is an effective way to improve email security and stop BEC attacks that rely on stolen credentials. MFA adds an extra step to logging in, such as a code from an authenticator app or a security key. Even if login credentials are exposed through phishing or data breaches, MFA can prevent unauthorized access to the account.
Enable MFA on all email accounts, not just executive ones. Attackers can start with lower-level employees whose inboxes contain useful information or can be used to move attacks internally. Finance, HR, and administrative roles should be protected just as carefully as leadership.
Choose strong authentication methods where possible. Authenticator apps and hardware security keys offer far better protection than SMS codes, which can be intercepted through SIM-swapping attacks.
Finally, make sure MFA also applies to remote access and third-party apps connected to your email system. Each integration is a potential entry point, so review connected apps regularly and remove anything that’s no longer needed.
Implement role-based email verification
Clear verification procedures help ensure that sensitive requests are confirmed before action is taken. This includes financial transfers, changes to payment details, and requests for confidential information.
Role-based verification means applying additional checks based on the type of request rather than who sent it. For example, payment changes or urgent financial approvals should always be confirmed through a secondary communication channel, regardless of whether the email appears to come from a senior executive or a trusted vendor.
Consider using dual approval for sensitive transactions. Requiring two people to sign off, ideally from different teams or through different channels, makes it much harder for attackers to succeed.
Finally, have documented verification steps to reduce reliance on individual judgment and make it easier for employees to pause and confirm unusual requests. You should also have a clear escalation path for anything that can’t be verified easily. If contact attempts fail or something feels off, employees should know exactly who to involve next.
Employee cybersecurity awareness training
Regular cybersecurity awareness training helps staff recognize social engineering red flags and understand when to slow down and verify a request.
Training should focus on realistic scenarios employees may encounter in their roles, such as urgent payment requests, unexpected account changes, or emails asking for sensitive data. Reinforcing these lessons over time helps normalize verification rather than treating it as an exception. Encouraging a culture where employees feel comfortable questioning unusual requests also reduces the effectiveness of authority-based impersonation.
Use of DMARC, SPF, and DKIM for email authentication
Email authentication protocols such as Domain-based Message Authentication, Reporting, and Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) help organizations reduce the risk of domain impersonation and email spoofing. These technologies allow receiving mail servers to verify whether an email claiming to come from a domain is authorized to do so. Here’s how they work:
- SPF defines which mail servers are allowed to send email on behalf of a domain. If a message comes from an unauthorized server, receiving systems can flag or reject it.
- DKIM adds a digital signature to outgoing emails, allowing recipients to verify that the message originated from the claimed sender's domain and wasn’t altered in transit.
- DMARC ties everything together by telling receiving servers what to do when SPF or DKIM checks fail and by providing reports that show who’s trying to misuse your domain.
When properly configured and enforced, these controls can block or flag many spoofed emails before they reach inboxes. However, they do not prevent all BEC attacks, particularly those that rely on compromised email accounts rather than domain impersonation. For this reason, email authentication should be treated as foundational hygiene rather than a standalone defense against BEC.
FAQ: Common questions about BEC attacks
Is BEC a cybercrime?
Business email compromise (BEC) is a serious cybercrime and is treated as such by law enforcement. BEC attacks often violate wire fraud, computer fraud, and identity theft laws. Because of the scale of financial damage involved, agencies like the FBI actively investigate these cases. That’s why organizations should always report BEC incidents to law enforcement, not just handle them internally.
Can AI make BEC attacks more dangerous?
AI can increase the realism and scale of certain social engineering techniques, such as generating more convincing emails or mimicking writing styles. However, the core risk factors behind business email compromise (BEC) attacks remain the same: trust-based workflows, insufficient verification, and human decision-making. As attacks become more realistic, strong verification processes, awareness training, and a culture of healthy skepticism become even more important.
How effective are security tools against BEC?
Traditional email security tools offer limited protection against business email compromise (BEC) because many attacks contain no malware, links, or attachments. Email authentication protocols like Domain-based Message Authentication, Reporting, and Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) help block simple spoofing, but they don’t stop attacks from compromised accounts or look-alike domains.
Since many BEC attacks rely on legitimate-looking messages and trusted accounts, tools alone aren’t enough. The most effective protection combines technical controls with clear verification procedures and informed employees.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN