What is OIDC (OpenID Connect)? A complete guide to understanding the identity layer

Every time we sign in to a new app or website, we share personal details like usernames, passwords, or contact information. Each login creates another opportunity for that data to be exposed, making secure authentication a key part of online safety.
That’s where OpenID Connect (OIDC) comes in. It simplifies how identity works on the internet, letting users prove who they are without constantly handing over sensitive information. In this guide, we look at what OIDC is, how it works, and why it’s become the trusted standard for safer, streamlined authentication.
What is OpenID Connect (OIDC)?
OIDC is an identity layer built on OAuth 2.0, a framework that allows apps to request limited access to user data on another service without sharing passwords. OIDC lets users log in through trusted providers like Google or Microsoft, so apps can verify identity without managing passwords directly.
OIDC underpins modern identity federation, which is the concept of allowing users to authenticate with a trusted identity provider (IdP) to securely access multiple systems or applications across various organizations.
Why OIDC was created
Before OIDC, online authentication was inconsistent. Developers often relied on OAuth 2.0, which was built for authorization rather than authentication. In other words, OAuth2.0 could grant access to data, but couldn’t confirm who the user actually was.
OIDC was created to fix two main problems:
- No identity layer in OAuth 2.0: OAuth 2.0 let apps request access to data but didn’t include a way to confirm who the user was. OIDC addressed this by introducing the ID token, which provides a standard, verifiable proof of identity.
- Complex design in OpenID 2.0: The older OpenID 2.0 system used outdated formats like XML and was difficult to adapt for web and mobile apps. OIDC replaced it with simpler tools like JavaScript Object Notation (JSON), a lightweight data format, and JSON Web Tokens (JWTs), which are compact tokens that encode a set of claims.
Common examples of OIDC
You might not realize it, but OIDC powers many of your everyday sign-in experiences:
Single sign-on (SSO)
A key use of OIDC is in SSO systems, which let users sign in once and access multiple apps securely.
- For everyday users: When you choose options like “Sign in with Google” or “Sign in with Apple,” you’re using OIDC. The app or website asks that provider to confirm your identity instead of handling your password directly.
- For businesses: In workplaces, OIDC allows employees to log in through one secure portal and access tools like Microsoft 365 or Salesforce instantly. It simplifies access and reduces the risk of password compromise by minimizing the need to create or store multiple passwords across various apps.
Enterprise and consumer integrations
OIDC is widely used as the standard framework for online identity. It’s used by:
- Consumer platforms: Google, Microsoft, Facebook, Apple, and PayPal
- Enterprise services: Okta, Auth0, Azure AD (Microsoft Entra ID), and Ping Identity
- Mobile systems: iOS and Android tools that enable password-free sign-ins
How does OIDC work?
OIDC defines a clear, standardized process for verifying identity through trusted providers, keeping authentication consistent and secure for both users and developers.
Understanding the OIDC authentication flow
OIDC works through a simple, secure interaction between three key roles:
- End user (resource owner): This is the person trying to sign in. They initiate the authentication process, typically by clicking a “Sign in” button, which then directs them to their chosen IdP to verify their identity. They ultimately own the account and data being accessed.
- Relying party (RP) or client: This is the app or website that needs to confirm who the user is. Instead of verifying the user directly, it sends a login request to a trusted provider and receives a digital proof, called an ID token, confirming that the user’s identity has been verified.
- OpenID provider (OP) or authorization server: This trusted service, also known as the IdP, handles the login itself. It authenticates the user and sends the ID token back to the app. Examples of OPs include Google, Okta, and Microsoft Entra ID.
Authorization code flow explained
The authorization code flow is the most secure and widely used method to manage authentication in OIDC. It’s designed for web apps that manage sign-ins on their own servers. Instead of sending sensitive login data through the browser, it uses a short authorization code that’s exchanged securely in the background.
Here’s how it works:
- The sign-in request: When a user tries to log in, the app sends them to a trusted provider such as Google or Okta to authenticate.
- Verification and consent: The provider confirms the user’s identity, often by asking for credentials or a second authentication factor, and may request consent to share certain profile details with the app.
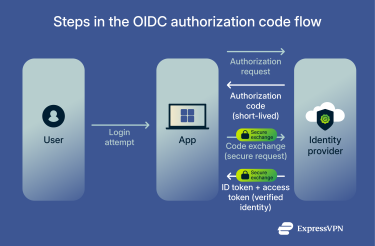
- The authorization code: After login, the provider redirects the user back to the app with a short-lived code. On its own, this code doesn’t reveal personal data or grant access.
- The secure exchange: Behind the scenes, the app’s server privately exchanges that code for two digital files: an ID token (to confirm who the user is) and an access token (to authorize limited actions). This extra step adds protection by keeping sensitive tokens out of the browser. Only the short-lived code travels through it, and it’s useless without the app’s private credentials.
Implicit and hybrid flows
Earlier versions of OIDC supported older sign-in methods built for web apps that couldn’t connect securely to a server:
- Implicit flow (now outdated): The implicit flow was once used by apps that ran entirely in the browser. It sent login tokens through the browser after users signed in, which made them easier to intercept. Because of this, implicit flow is no longer considered secure and has been replaced by the authorization code flow with Proof Key for Code Exchange (PKCE), a feature that adds a critical layer of protection during exchange to keep tokens private.
- Hybrid flow: The hybrid flow combined parts of both the implicit and authorization code methods. It let apps get some information right away in the browser, while still exchanging other details privately on the server. Although it offered better protection than the implicit flow, the authorization code flow with PKCE is now the preferred method for reducing the risk of exposing sensitive data.
Tokens and claims in OIDC
OIDC uses secure tokens, usually in the form of JWTs, to exchange verified identity and permission information. Each token contains claims: short, verifiable pieces of information such as a user ID, email address, or login timestamp. These tokens let apps confirm identity and permissions without handling passwords directly.
Key components of OIDC
Several key parties work together in the OIDC process. Each plays a distinct role in verifying identity and granting access securely.
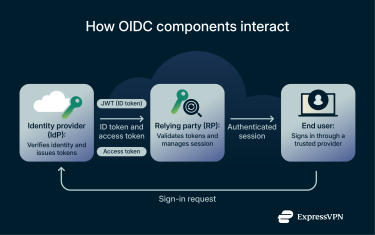
Identity provider (IdP)
The IdP is the trusted service that confirms who a user is. It manages accounts, protects credentials, and runs the sign-in so individual apps don’t handle passwords.
The IdP :
- Handles authentication: The provider checks credentials and extra steps like passkeys or one-time codes. The app never sees these secrets.
- Issues tokens: After a successful login, it returns an ID token to prove identity and may also return an access token for limited actions.
- Manages consent and policy: It can ask the user to approve what an app may see or do, and it records that choice.
- Enables verification: It publishes simple setup details and public keys so apps can send requests to the right place and verify that tokens are genuine.
- Supports session controls: It can signal when a session starts or ends, helping apps keep users signed in or log them out securely and consistently.
Relying party (RP)
The RP is the app or website that depends on the IdP to verify users. After the IdP confirms a login, the RP validates the received token and establishes a secure session.
Once verified, the RP can safely use the information in the token, such as a username or ID, to personalize the user experience.
ID token, access token, and UserInfo endpoint
Once authentication succeeds, the IdP issues tokens that confirm identity and define permissions:
- ID token: Verifies who the user is, and contains details like user ID, authentication time, and issuer.
- Access token: Specifies what actions the app is allowed to perform on the user’s behalf.
- UserInfo endpoint: Lets the app request extra verified user data (e.g., email, name) using the access token.
Benefits of using OIDC
OIDC reduces the risk of password compromise and gives users control over what data they share. For organizations, it simplifies access management and strengthens authentication.
Benefits for end users
- Seamless SSO: Log in once with a trusted provider like Google or Microsoft and access multiple apps without creating new accounts.
- Fewer password risks: Since users don’t need to manage separate passwords for every app, they’re less likely to reuse weak credentials. However, it’s still essential that the user’s main SSO password is strong and unique.
- More privacy and control: OIDC asks for user consent before sharing information, so people can choose what details to share and revoke access at any time.
Benefits for organizations and developers
- Centralized security: IdPs handle login, multi-factor authentication (MFA), and password protection. By consolidating these functions, they reduce the risk of compromised accounts and make compliance with regulations such as the General Data Protection Regulation (GDPR) easier to manage.
- Built for modern apps: OIDC works through lightweight web standards such as JSON, making it ideal for mobile and cloud-based apps.
- Simplified identity management: Teams can manage user access and permissions from a single system, improving visibility and reducing maintenance work.
OIDC vs. other authentication protocols
Here’s how OIDC compares with the other major authentication and authorization systems.
OIDC vs. OAuth 2.0
In simple terms, OAuth 2.0 focuses on what an app is allowed to do, while OIDC focuses on confirming who the user is.
OAuth 2.0 handles authorization, letting an app act on a user’s behalf without ever seeing their password; for example, it could allow a calendar app to read your Google Calendar events after you grant permission.
OIDC adds authentication, the missing piece that verifies a user’s identity through a trusted provider and confirms that the person logging in is really who they claim to be.
OIDC vs. SAML
Before OIDC became the preferred standard, many organizations used Security Assertion Markup Language (SAML) to manage SSO across their systems. Both of these methods handle secure logins, but their design and purpose come from different generations of technology.
Here are the main differences:
- Data format: SAML uses XML, a heavy and complex format built for older web systems. OIDC relies on lightweight JSON, which is easier to read, faster to process, and better suited for mobile and cloud apps.
- Integration: SAML was designed for traditional, browser-based setups that often require manual configuration. OIDC uses modern web standards like HTTPS and Representational State Transfer (REST), making it simpler to connect with APIs and newer platforms.
- Use cases: SAML remains common in large enterprises and government systems that depend on legacy infrastructure. OIDC is the go-to choice for modern, cloud-based applications and mobile environments.
OIDC vs. LDAP
Lightweight Directory Access Protocol (LDAP) is a long-established system used by organizations to manage user accounts and directory information. While OIDC manages authentication, confirming who a user is and enabling secure sign-ins, LDAP acts as the underlying directory that stores those user records for reference by other systems.
The main differences are:
- Purpose: OIDC manages authentication, confirming who a user is and handling secure sign-ins through encrypted tokens. LDAP stores user details such as names, emails, and passwords in a central database that other systems can reference.
- Operation: OIDC uses modern web standards like HTTPS and token-based exchanges. LDAP relies on direct username-and-password checks.
- Security and scope: OIDC supports MFA and is built for cloud and mobile environments. LDAP was developed for internal networks and requires additional encryption to protect communications.
| Feature | OIDC | OAuth 2.0 | SAML | LDAP |
|---|---|---|---|---|
| Main purpose | User authentication | App authorization | Enterprise SSO | Directory management |
| Data format | JSON/JWT | Opaque tokens (often JWTs) | XML | Directory entries |
| Best suited for | Cloud and mobile apps | API access | Legacy enterprise systems | Internal networks |
When to use each
Many systems use both OIDC and LDAP. The IdP can check a user’s credentials against an LDAP directory during login. Once verified, OIDC issues a secure ID token that allows access to apps without exposing passwords or depending on internal systems.
If you’re choosing an identity approach, consider your app type and the systems you need to connect to. Here’s a general guide:
Choose OIDC when you need:
- Web or mobile sign-ins for browser apps, single-page applications (SPAs), iOS, or Android.
- Secure access to APIs and microservices.
- SSO with popular IdPs for consumers or employees.
- Cloud or hybrid setups where apps run across devices and networks.
Choose SAML when you need:
- Integration with an existing enterprise SSO that already runs on SAML.
- Compatibility with browser-based, server-rendered applications.
Choose LDAP when you need:
- A central directory to store users, groups, and attributes inside a private network.
- A backend source your IdP can query to verify passwords or look up user details.
Common implementation challenges
OIDC simplifies authentication in theory, but putting it into practice can be tricky. Most challenges come from handling tokens securely, integrating with older systems, and maintaining performance as user numbers grow.
If these areas aren’t managed well, they can weaken the security and reliability that OIDC is designed to provide.
Security and token handling
A major challenge in OIDC implementation is keeping tokens and secrets secure after authentication. Missteps in how tokens are validated, stored, or rotated can expose vulnerabilities that compromise user data. Here are some common issues:
- Complex setup: OIDC comes with specific flows, tokens, and configuration steps. It’s easy to mix them up or overlook a small detail that might break sign-in.
- Security slip-ups: Misconfiguring tokens or secrets can leave gaps attackers could exploit. A missing validation check or exposed secret can weaken security.
- Debugging: When something goes wrong, OIDC error messages can be vague, making it hard to spot what failed or where.
Each of these challenges can be managed with careful setup and testing, but they’re part of what makes implementing OIDC more complex than it looks at first glance.
Integration with legacy systems
Some organizations still depend on applications built with older identity standards such as SAML. Connecting these systems with OIDC can be difficult, as each uses different data representations and authentication mechanisms.
Modern IdPs can bridge the gap via protocol translation or identity gateways, which lets legacy systems participate in modern SSO flows. However, this introduces additional configuration, mapping, and testing complexity.
Scalability considerations
Because OIDC involves several network steps, small delays can quickly add up under load.
Key scalability challenges include:
- Token verification load: Every request requires validating access and ID tokens, which increases processing time under heavy traffic.
- Frequent JSON Web Key Sets (JWKS) fetches: Continuously retrieving public keys from the IdP can slow performance if caching isn’t handled efficiently.
- Session management at scale: Tracking active sessions for many users or apps adds complexity, especially when sessions need to stay synchronized across servers.
- Token refresh handling: Managing token lifecycles safely while minimizing unnecessary reauthentication requires a careful balance.
- Multi-tenant environments: Supporting multiple apps or clients in a shared system increases configuration load and the chance of security issues.
Best practices for relying parties
In OIDC, the IdP authenticates the user. Your app (RP) must verify tokens and keep the session secure and stable. Here’s how:
Validate tokens
- Verify the signature: Use the IdP’s public keys to ensure the ID token has not been tampered with and was issued by a trusted provider.
- Check issuer and audience: Confirm the iss (issuer) claim in the token matches the expected IdP, and that the aud (audience) claim corresponds to your app’s ID.
- Enforce timing: Reject tokens that are expired (exp) or not yet valid (nbf).
- Use state and nonce: State is a unique, random value sent with each login request to prevent cross-site request forgery (CSRF) attacks. Nonce, in this context, is a one-time string included in the authentication request and verified in the ID token to protect against replay attacks.
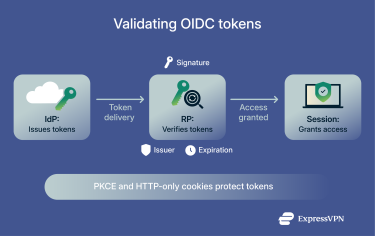
Handle setup and storage safely
- Use PKCE: PKCE helps protect the code exchange in browser and mobile apps.
- Keep secrets server-side: A client secret is a private key shared between your app and the IdP, used to prove that requests really come from your app. Keep them server-side if you have a backend, and never expose them in client code.
- Avoid local storage for tokens: Prefer memory or secure HTTP-only cookies to reduce the risk of cross-site scripting (XSS) attacks, where malicious scripts injected into a webpage can steal sensitive data such as tokens.
- Rotate keys regularly: This minimizes the impact of potential leaks.
- Monitor token use: This helps to detect unusual patterns, such as reuse or expired-token access attempts.
Optimize performance and scalability
An efficient setup helps OIDC stay responsive as usage grows. These steps can keep authentication fast and stable without weakening security:
- Cache public keys locally: Store the IdP’s JWKS instead of fetching them for every request to speed up token validation.
- Minimize extra calls: Include key user details in the ID token to reduce queries to the UserInfo endpoint.
- Balance security and continuity: Use short-lived access tokens with refresh tokens to maintain sessions without constant reauthentication.
- Plan for multi-tenant environments: Use Dynamic Client Registration so new apps can register automatically with the IdP.
FAQ: Common questions about OIDC
What is the difference between OpenID and OIDC?
OpenID was an earlier authentication protocol that allowed users to sign in across websites but relied on older, less standardized methods. OpenID Connect (OIDC) modernizes that approach by building on OAuth 2.0, using JavaScript Object Notation (JSON) and JSON Web Tokens (JWTs) for secure, verifiable identity exchange across modern web and mobile apps.
Why do we need OIDC?
OpenID Connect (OIDC) adds an identity layer to OAuth 2.0, letting apps confirm who a user is, not just what they can access. It standardizes authentication so users can log in securely with trusted providers instead of sharing passwords with every app or service they access.
Can OIDC be used for API authentication?
Yes. While OpenID Connect (OIDC) primarily handles user authentication, it works alongside OAuth 2.0 to secure API access. It issues ID tokens for verifying user identity and access tokens that APIs can use to authorize requests, allowing secure access without exposing user passwords.
How do you implement OIDC in an application?
Apps implement OpenID Connect (OIDC) by integrating with a trusted identity provider (IdP) using the authorization code flow. The app redirects users to the IdP for login, receives an authorization code, then exchanges it for tokens to verify identity securely.
Is OIDC the same as single sign-on (SSO)?
Not exactly. OpenID Connect (OIDC) is the protocol that enables secure identity verification, while SSO is one of its main use cases. SSO lets users access multiple apps with one verified login, using OIDC as the framework for seamless, password-free authentication.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN