What is quantum encryption? How it works and why it matters

As the age of quantum computers approaches, it brings both exciting opportunities and new challenges for consumer technology. One is that quantum computing has the potential to break otherwise solid encryption methods. For this reason, experts point to the need for quantum encryption to counter the threat.
The details are very technical, but it’s important for average users to understand what’s at stake with a potential quantum transition. This guide aims to assist, answering the questions of what quantum encryption is, how it works, and what it has to offer.
Understanding quantum cryptography
What is the difference between quantum encryption and traditional encryption?
Both conventional and quantum cryptography convert data into randomized strings that can only be deciphered with the aid of a key. Without that key, anyone who intercepts the data won’t be able to read it.
However, they work in notably different ways, with quantum representing a major step forward in the history of cryptography.
Conventional encryption is based on mathematics. It involves creating mathematical problems that are incredibly complex and therefore costly and time-consuming to solve. This protects data from being decrypted by anyone other than the intended recipient.
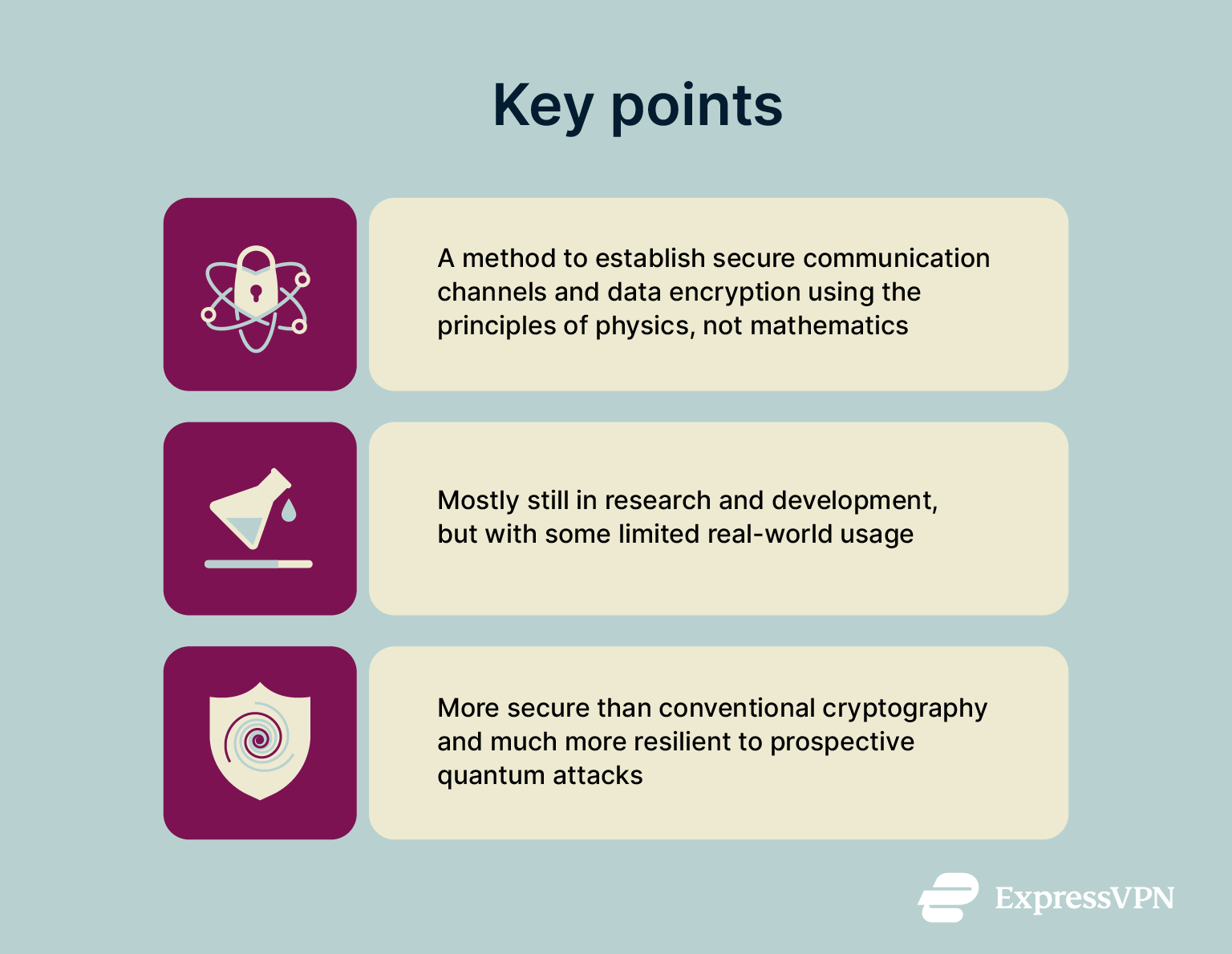
Quantum encryption, meanwhile, is based on the laws of physics. In theory, when implemented correctly, it can be secure against any attempt to break it. This is because it depends on fundamental physical principles rather than on the limits of computing power.
Why quantum encryption is considered more secure
Quantum encryption is considered more secure than traditional encryption due to the nature of the principles involved. To understand why, it’s helpful to first look into the problems associated with older methods.
Conventional encryption works not because its formulae are impossible to solve, but because solving them would take vast amounts of resources. Even with all the world’s current computing power working together, cracking the best standard of conventional encryption would likely take more time than the lifespan of the universe.
But quantum computers, which are likely to become at least somewhat prevalent in the future, could potentially avoid this resource problem and crack most forms of conventional encryption. To prepare for this, ExpressVPN has integrated Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM), a post-quantum technology, into its Lightway protocol. We’ve also developed a way to future-proof the WireGuard protocol against quantum threats.
By its very nature, quantum encryption has strong defenses against eavesdropping or snooping. This is because it revolves around the use of photons, which change state when they are observed. As such, if any unauthorized third party attempts to access or view quantum-encrypted data in transit, it will instantly change state, alerting the end users of the eavesdropping attempt.
How does quantum encryption work?
Key principles of quantum mechanics used in encryption
Quantum encryption relies on several complex principles of quantum mechanics, namely:
- Superposition: This refers to the ability of qubits (the quantum equivalent of bits) to exist in multiple possible states at the same time. Superposition allows for more information to be encoded with qubits than classical bits.
- Entanglement: This is the ability of two or more qubits to be joined together, even when separated by physical distances, and share the same fate, allowing for the creation of theoretically unbreakable encryption.
- Uncertainty: Heisenberg’s uncertainty principle refers to the fact that it is impossible to precisely measure all of a particle’s properties simultaneously, and any attempt to measure a particle’s state will invariably alter that state.
What is quantum encryption, and how does it work?
Quantum encryption, or quantum cryptography, is a method of encryption that relies on the principles of physics, not mathematics, to encrypt data. It relies on photons (light particles) to transmit keys from one point to another via a fiber optic cable.
There are numerous possible quantum encryption methods, and each works differently. Below, we’ll look at the steps involved in the best-known method: quantum key distribution (QKD):
- The photons leave the sender and pass through a filter, or polarizer, which assigns them one of several possible states before traveling to a receiver at the other end.
- There, a beam splitter and detectors randomly measure the incoming photons.
- The measured information is then transmitted between the sender and receiver over the public channel. This is used to form and confirm the encryption key to decrypt the data.
Real-world applications of quantum encryption
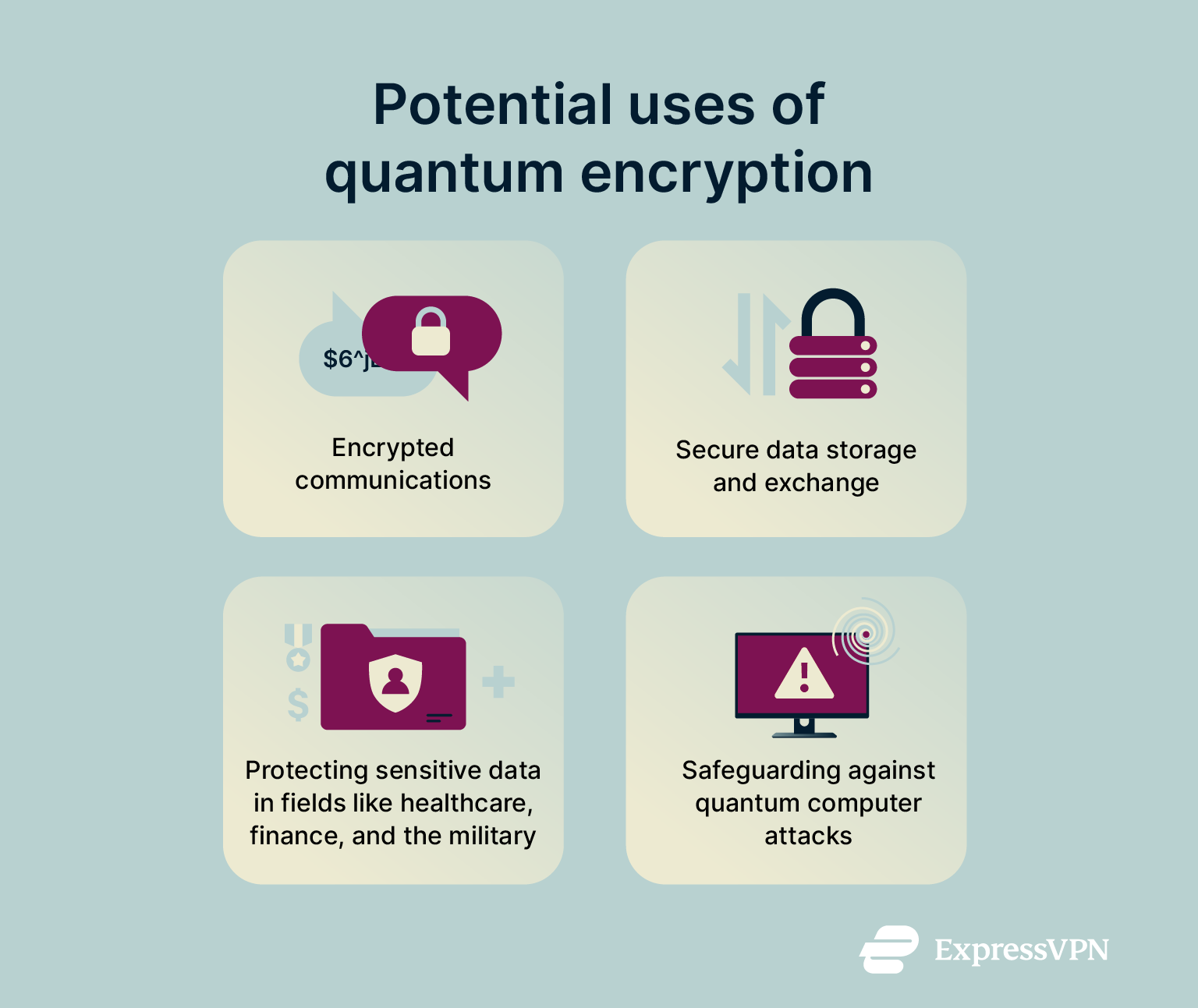
What is an example of quantum encryption?
QKD is the best-known example of quantum cryptography. It relies on the principles of quantum mechanics to allow two parties to exchange encryption keys in a highly secure way, with any attempt at interception being observable to the sender and intended recipient.
Who is using quantum encryption today?
Quantum encryption is largely still in the research and development phase. It has not reached anything close to widespread adoption in any field or industry. However, it is being tested and used in specific sectors and environments.
To be more precise, telecommunications companies and certain other large firms have carried out QKD trials and begun implementation of QKD technology.
Quantum encryption in government and military sectors
Multiple governments and military forces around the world are investing in research and development of quantum encryption and exploring their own strategies to adopt the technology.
This is largely due to the threat of cyberattacks using quantum computers, as well as the many utilities of quantum encryption for secure data storage and communications. For the moment, this danger is largely theoretical, but as quantum computing becomes widespread, the threat will become very real.
Advantages and limitations of quantum encryption
Benefits of using quantum encryption
- Advanced security: Quantum encryption has the potential to be far more secure than any existing conventional encryption method. Relying on the principles of physics, rather than mathematical formulae, it can create secure connections that are theoretically impossible to break.
- Instant detection of eavesdropping: If any third party attempts to read or access data encoded via quantum cryptography, the end users will immediately be informed. The quantum state of the data will change the moment it is observed, essentially issuing an alert to the parties involved at each end.
- Versatile protocols and far-reaching applications: Quantum cryptography technology is complex and versatile, with a range of methods and algorithms in development. These include QKD, quantum digital signatures, quantum secret sharing, and quantum secure direct communication.
Current limitations and technical challenges
- Limited range: Certain forms of quantum communications, such as QKD, have limited range, currently estimated at around 400 to 500 kilometers (250 to 300 miles). This is due to the fact that photons may be lost or absorbed as they travel long distances.
- Expensive: Quantum cryptography needs specialist hardware, such as photon emitters and detectors, as well as dedicated optical fiber connections. It is therefore quite costly compared to more traditional encryption technologies.
- Risk of errors: Photons can be scattered or lost in transit and may change polarization as they travel, which could lead to encryption errors when they arrive at the other end of the communication tunnel. The risk of errors tends to rise with more long-distance connections.
The future of quantum encryption
Will quantum break encryption?
It is expected that quantum computers will be able to break many (if not all) current encryption methods. This is due to the fact that their processing power will far surpass that of current computers. However, cryptographic developers are already at work on post-quantum cryptography (PQC) algorithms that should be able to withstand even attacks from quantum computers.
The race toward quantum-safe algorithms
As quantum computing technology develops, there is a concerted effort to develop and deploy effective cryptographic technologies that can resist attacks from quantum computers. Methods that rely on a potential hacker lacking sufficient computational resources to crack a code could be vulnerable to advanced quantum attacks.
Emerging trends in quantum communication
Quantum communication technology is evolving rapidly, with key trends including:
- Ongoing advancements in QKD.
- Development of quantum teleportation, or the ability to transfer quantum information without physically transmitting the quantum carrier.
- Construction of large-scale quantum networks and the infrastructure needed to create them.
Key terms in quantum encryption
What is quantum key distribution (QKD)?
QKD is a secure method for two parties at either end of a connection to exchange cryptographic keys, powered by the principles of quantum mechanics. It involves a quantum channel to transmit quantum states, encoded with data that makes up the secret keys. QKD is strong enough to withstand attacks even from quantum computers. Indeed, our current understanding of physics suggests that, if properly implemented, QKD would be impossible to crack.
What is superposition in encryption?
Superposition is a principle of quantum mechanics. It refers to a quantum system's ability to exist in multiple states at the same time. In the field of quantum encryption, the principle of superposition is harnessed for QKD protocols to create secure connections.
FAQ: Common questions about quantum encryption
Who invented quantum encryption?
Stephen Wiesner was one of the early pioneers to explore the concept of quantum cryptography in the 1960s, but Charles H. Bennett and Gilles Brassard were the first to build on Wiesner’s ideas and put them into action, creating the first quantum key distribution protocol in the 1980s.
When will quantum encryption become widely adopted?
There’s no fixed date for the widespread adoption of quantum encryption. However, many governments are exploring plans to implement post-quantum cryptography (PQC) by 2035. It may take several years or even decades before quantum encryption is widely adopted.
Can current encryption methods withstand quantum attacks?
No, generally speaking, most of today’s encryption methods are susceptible to quantum computer attacks. This highlights the need for ongoing focus and investment in quantum cybersecurity encryption technologies.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN