What is a dumpster diving attack in cybersecurity?

Most people think of trash as the end of the line, but in cybersecurity, it can be the starting point for some malicious actors. Instead of (or in addition to) hacking digital systems, dumpster diving attackers focus on discarded information that can be used to access accounts, networks, or personal data.
In this article, we’ll explore what a dumpster diving attack is, why it remains a relevant cybersecurity risk, and how individuals and organizations can protect themselves against it.
What is a dumpster diving attack?
Dumpster diving in cybersecurity generally refers to the practice of searching through physical or digital waste to find useful information that still contains valuable information. This can include paperwork with login credentials, internal documents, or operational material, and old devices or storage media that haven’t been properly wiped or destroyed. The common risk is assuming that once information or equipment is thrown away, it no longer poses a security concern.
Why dumpster diving is considered a physical security threat
Dumpster diving is primarily a physical security threat because its weak point lies in how people and organizations handle information outside digital systems. If someone can access areas where sensitive materials are discarded, whether through public access or inadequate controls, there's no need for malware, hacking tools, or network access.
This risk often occurs in areas treated as routine or operational, such as disposal areas, recycling bins, or storage rooms for retired equipment. Once information passes through these locations, it can leave secure control and become a source of data for follow-on attacks like impersonation or social engineering.
Why physical security still matters in cybersecurity
Dumpster diving illustrates a broader issue: that sensitive data doesn’t only exist online. Paper records and retired devices can expose information long after they’re no longer in active use, even when digital security measures are otherwise strong.
Because physical access can sometimes offer limited visibility, even minor lapses in handling or disposal can lead to real-world consequences, including fraud and identity theft. Securely disposing of important records and devices helps close the gap that technical controls alone can't address.
How dumpster diving attacks are carried out
Dumpster-diving attacks are low-tech but potentially high-impact cybersecurity threats that generally follow a straightforward process.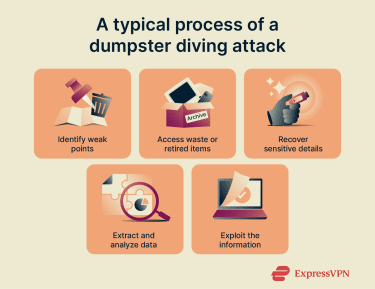
- Identify disposal hotspots: Attackers target locations where sensitive documents or retired equipment are routinely trashed or temporarily stored before removal. This often includes less-monitored public or semi-public areas such as loading docks, mailrooms, or vendor collection points.
- Collecting discarded items that look useful: They gather boxes, folders, or devices that seem to belong to the target. Paperwork, shipping labels, internal forms, and bundled records from office cleanouts are prime targets. This can also include devices and storage media that haven’t been properly wiped.
- Examining and reconstructing valuable information: Next, attackers sift through the collected items to locate readable or recoverable data, such as names, addresses, account details, contact lists, or documents revealing internal routines and processes.
- Piecing together a detailed profile: Even small bits of information can add up. By combining scraps, attackers may be able to build profiles detailing identities, relationships, used services, and security questions or verification details that can be exploited.
- Leveraging the gathered information for follow-up attacks: The harvested data is usually used for impersonation and social engineering. This can include posing as employees or customers to contact companies, attempting to recover accounts with personal details, or crafting targeted phishing attacks that appear credible because they reference real information.
Why dumpster diving attacks are dangerous
The consequences of dumpster-diving attacks can be severe for organizations and individuals, especially when certain types of sensitive information are found and used to support follow-on attacks.
Types of information targeted in dumpster diving
Common targets include:
- Personal identification documents: Paperwork that includes personally identifiable information such as names, addresses, dates of birth, or government-issued identifiers. Even partial data can be reused or combined with other details to impersonate someone or pass basic verification checks.
- Financial records: Bank statements, billing notices, credit card paperwork, invoices, or pre-approved offers. These documents often contain account references or financial context that can be exploited even if they’re not recent.
- Medical or insurance documents: Records that expose health information, policy numbers, or provider details. This type of data is especially sensitive and can be misused for medical fraud or targeted impersonation.
- Employment and business paperwork: Internal memos, organizational charts, payroll-related documents, access codes, financial reports, or client details. These materials can reveal how an organization operates and who has access to specific systems or data.
- Discarded devices and storage media: Computers, phones, hard drives, USB devices, or backup media that still retain data if they were not properly cleared before disposal.
- Other seemingly harmless information: Attackers can piece together details from items like calendars, meeting notes, network diagrams, organizational charts, printed emails, and telephone directories. By assembling these fragments, they build a backstory that helps establish trust and gain unauthorized access to organizational resources.
How discarded data leads to identity theft and fraud
The Federal Trade Commission (FTC) has warned of the link between dumpster diving and identity theft and fraud.
Discarded data becomes dangerous because misuse is difficult to detect. Unlike digital intrusions, there are no login attempts, alerts, or security logs when someone accesses information from a disposal area. Physical access may leave little to no trace of the attacker’s actions.
As a result, discovery is often delayed. Individuals may only realize something is wrong after unexplained account activity, missing mail, or services they did not request. Organizations may learn of exposure weeks or months later through customer complaints, regulatory inquiries, or third-party notifications.
Without knowing when the data was accessed or exactly what was taken, it becomes more difficult to contain the damage or prevent further misuse.
The risk is compounded by how discarded information is used. Details taken from thrown-away materials can support impersonation, account takeovers, password resets, or fraudulent requests that rely on familiarity with internal processes or personal history.
Common dumpster diving risks for individuals and businesses
Dumpster diving exposes sensitive information differently depending on whether it targets individuals or organizations.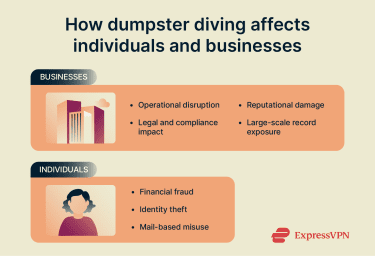
Personal information exposure
Household trash often contains various personal documents, such as bank statements, insurance paperwork, medical letters, school records, and shipping labels. Even older or seemingly insignificant documents can provide enough clues to facilitate identity theft or fraud.
Beyond direct financial loss, exposed medical information or insurance details can lead to privacy breaches and targeted scams. Address details can also be misused in mail fraud, such as intercepting bills or redirecting services. Victims often face ongoing uncertainty and stress, as it’s difficult to know exactly what information was compromised or how it might be exploited.
Learn more: Read our detailed identity theft prevention guide.
Business and corporate data leakage
Organizations face broader risks when sensitive data is improperly discarded. This may include customer and employee information, internal communications, or operational details that reveal business processes. Such exposures can harm a company’s reputation and trustworthiness, trigger costly internal investigations, and require cross-departmental response efforts involving IT, legal, and HR.
Furthermore, organizations often depend on third-party vendors for waste handling or equipment disposal, which can complicate control over sensitive materials. Even a single disposal mistake could potentially lead to a large-scale data breach.
Learn more: Find out how to protect yourself against employment identity theft.
Risks from discarded devices and storage media
Unlike paper, electronic devices and storage media retain data even after disposal if not properly wiped. Equipment set aside for recycling, resale, or donation may pass through multiple hands, increasing the risk of unauthorized access.
A single device containing credentials or confidential files can expose critical data. Proper data sanitization before disposal is essential to prevent such breaches. Regulatory penalties, such as the Securities and Exchange Commission (SEC)’s $35 million fine against Morgan Stanley Smith Barney for improper device disposal, highlight the serious consequences of neglecting these risks.
How to prevent dumpster diving attacks
Preventing dumpster diving attacks comes down to one principle: discarded information should not remain usable. The most effective safeguards focus on what happens at the end of the information lifecycle, before paperwork or devices leave your control.
The steps below reduce risk by making sensitive material unreadable or unrecoverable and by helping ensure disposal is handled consistently rather than informally.
Secure document disposal practices
Paper records remain a common source of data leaks due to their widespread use and the ease with which they can be overlooked for proper disposal. Documents containing identifying, financial, medical, or internal business details should be considered sensitive until properly destroyed.
Individuals
- Shred paperwork related to banking, insurance, healthcare, taxes, and official correspondence.
- Reduce readability by thoroughly tearing documents when shredding isn't available, recognizing that it's less secure than shredding.
- Take extra caution during cleanups or moves when bulk discards are more likely.
Businesses
- Use locked collection bins or secure consoles to separate sensitive documents from general waste.
- Apply consistent disposal processes rather than relying on individual judgment about document sensitivity.
- Maintain regular document destruction schedules instead of one-time or audit-triggered efforts.
Proper disposal of devices and storage media
Devices and storage media require different handling than paper because data can persist even after files appear deleted. Smartphones, computers, external drives, and removable media sometimes retain recoverable information long after use ends.
Individuals
- Wipe smartphones and computers with a full factory reset before they're sold, donated, recycled, or discarded.
- Remove saved accounts, credentials, and personal files before disposal.
- Clear USB drives, memory cards, or external drives prior to disposal.
Learn more: Find out how to safely factory reset an iPhone or Mac.
Businesses
- Verify data removal using recognized media sanitization standards, such as the National Institute of Standards and Technology (NIST) SP 800-88, before devices are reassigned, retired, recycled, or destroyed.
- Maintain disposal records and certificates of destruction or sanitization.
- Avoid informal transfers or disposal of devices outside the organization’s approved process.
Employee awareness and security policies
Prevention mostly comes down to awareness and consistent disposal routines, including:
- Defining what information requires controlled disposal and what counts as sensitive within organizations.
- Establishing disposal procedures for paper and devices, restricting access to waste-handling and storage areas, and clearly assigning responsibility.
- Training employees to recognize sensitive material and route it to the appropriate disposal process.
- Training temporary staff, cleaners, and contractors who handle waste or equipment in the same security practices.
FAQ: Common questions about dumpster diving attacks
What types of information are commonly targeted in a dumpster diving attack?
Attackers look for information that still has context and practical value. This often includes documents with personal identifiers, financial details, or internal references, such as banking, healthcare, insurance, or employment paperwork. Discarded devices and storage media are also targeted. Phones, computers, and external drives may still contain files, saved credentials, or account data if they were not properly cleared before disposal.
Why is dumpster diving a security risk?
Dumpster diving is a security risk because sensitive information can remain accessible long after it has been discarded. Documents, devices, or storage media thrown away during routine cleanups may still contain personal, financial, medical, or operational data. When this information leaves controlled environments through normal disposal channels, it can be accessed without triggering alarms, logs, or other security controls.
Can dumpster diving lead to a data breach?
Yes. Dumpster diving can result in a data breach when discarded information exposes personal, customer, or internal data. Because access happens quietly and outside monitored systems, the impact is often discovered only after misuse has already occurred.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN