-

What is a script kiddie? How they attack and why it matters
“Script kiddies” is typically a derogatory term used to describe people who use ready-made hacking tools to launch attacks, lacking the skills to create their own. In the past, that lack of skill ...
-
What is password cracking and how can you prevent it?
Password cracking is a technique attackers use to uncover passwords by systematically guessing them or analyzing stolen, hashed password data. Weak or reused passwords make the process far easier than...
-

What is swatting and how can you prevent it?
Swatting is a dangerous form of harassment that exploits emergency services. It involves making false reports to trigger armed police responses at a specific address. These incidents often target stre...
-
How to spot and avoid the SunPass toll scam
Phishing scams impersonating SunPass have been widely reported since 2024, amid a broader rise in toll-related fraud across the U.S. By early 2025, the FBI had logged tens of thousands of complaints r...
-
How to identify and avoid Discord scams
From gaming servers to study groups and work communities, Discord has become a daily communication tool for millions of people. That popularity also makes it a target for scammers. Discord scams are d...
-
How to detect and prevent barrel phishing attacks
Barrel phishing attacks unfold slowly and rely on your attention, your routine, and the moments when you least expect manipulation. Even strong security tools can’t replace your own awareness, espec...
-

Is WhatsApp HIPAA compliant?
WhatsApp is widely used among medical staff, but many healthcare professionals question whether it meets the Health Insurance Portability and Accountability Act (HIPAA) rules and regulations. Healthca...
-
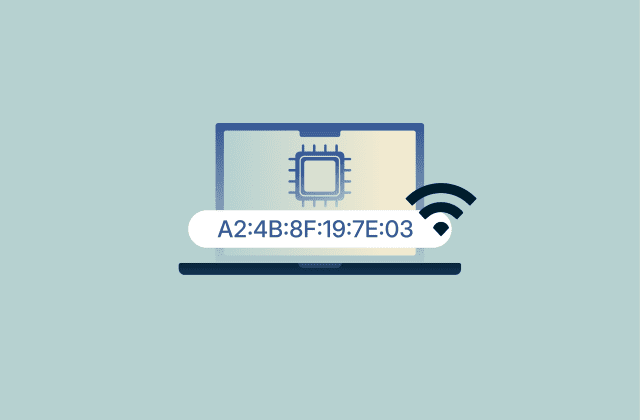
What is a MAC address and why does it matter?
A Media Access Control (MAC) address is a unique identifier that helps your device connect to and communicate on a local network. Whenever your phone, laptop, or smart gadget joins Wi-Fi or pairs with...
-

Is Brave browser safe? Everything you need to know about its privacy and security
Brave positions itself as a privacy-focused browser, but does that mean it’s any safer than more popular options like Chrome and Firefox? In this overview, we’ll analyze how Brave handles tracking...
-

Understanding IoT attacks and how to protect your devices
Internet of Things (IoT) devices make everyday life more convenient by connecting items like appliances, sensors, and tools to the internet. But this constant connectivity also creates new security ri...

This content is not available in your region
To continue, please visit our dedicated website for the United Arab Emirates.
ExpressVPN for UAE
