NDR vs. XDR: Key differences and how to choose
Cybersecurity tools keep evolving, and so does the terminology around them. Network detection and response (NDR) and extended detection and response (XDR) are two approaches that can overlap in their outcomes (improving detection and response), but they differ in the scope of visibility they aim to provide.
This guide explains NDR vs. XDR in clear terms, shows where each fits in modern security architecture, and outlines when one approach may make more sense than the other.
What is Network detection and response (NDR)?
NDR is a security tool that monitors network traffic as it moves between systems to identify potentially malicious activity. It typically analyzes packets or traffic metadata to learn normal patterns and alert on anomalies.
Because NDR operates at the network level, it can surface activity that endpoint-focused tools may miss, though in heavily encrypted environments, it may rely more on metadata and behavioral signals than payload inspection.
What NDR detects
NDR is particularly effective at spotting threats after initial access, when attackers start moving internally. Common detection scenarios include:
- Lateral movement: Identifying attackers as they move between internal systems or segments.
- Command-and-control (C2) activity: Detecting unusual outbound connections or beaconing patterns to external infrastructure that may indicate remote control.
- Behavioral anomalies: Flagging communications that deviate from established baselines, such as unusual data transfers or access patterns.
NDR provides visibility into both east-west traffic (internal communication) and north-south traffic (traffic entering or leaving the network), with particular strength in detecting suspicious activity within the network. Some attacks may not trigger endpoint alerts early on, but they can leave traces in how systems communicate with each other.
For example, if an attacker compromises one server and then connects to a database or file share, that internal movement may not trigger endpoint alerts but can still be visible in network traffic patterns. Another common signal is unusual outbound behavior, such as a host repeatedly “checking in” to an unfamiliar external domain or IP address in a regular pattern.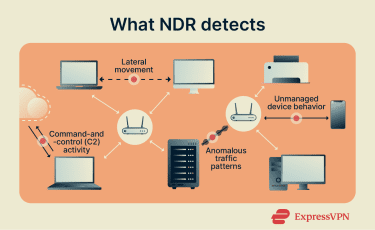
How NDR monitors network activity
Most NDR tools continuously monitor and correlate network activity over time, rather than evaluating traffic in isolation. They typically ingest data from network taps, traffic mirrors, and/or flow logs, which allows them to observe activity with minimal impact on latency (though collection and storage can add some overhead).
From there, NDR platforms apply analytics to model normal network behavior over time. Many use behavioral analytics and machine learning (alongside statistical methods) to flag anomalies that may indicate reconnaissance, credential abuse, or lateral movement.
Because NDR doesn’t require agents, it can help monitor devices that traditional endpoint detection tools can’t cover, such as printers, cameras, industrial systems, and unmanaged smart devices, which are often discussed in the context of Internet of Things (IoT) cybersecurity challenges.
With more traffic encrypted, NDR often leans on metadata (timing, volume, and destinations) to spot behavioral patterns, so it’s strongest at detecting “how” systems communicate, not necessarily “what” was transmitted
Where NDR fits in a security stack
NDR isn’t designed to replace existing cybersecurity tools. It works best as a complementary layer that fills visibility gaps.
In many environments, NDR sits alongside firewalls, endpoint detection tools, and security information and event management (SIEM) platforms. While firewalls enforce access controls and block policy-violating traffic, and endpoint tools monitor individual devices, NDR adds context on how systems communicate across the network. SIEMs can aggregate and correlate data from many sources, but NDR specializes in behavioral analysis of network traffic (packets/flows/metadata), which can provide additional detection context.
Understanding how a network is structured is important here. Clear segmentation and visibility into traffic paths make NDR alerts easier to interpret, which is why network mapping and segmentation context help.
What is extended detection and response (XDR)?
XDR is a security platform that collects and correlates telemetry from multiple security tools to improve detection, investigation, and response. Rather than focusing on one layer of the environment, it can provide coordinated visibility across endpoints, networks, cloud services, and identity-related activity.
XDR extends endpoint detection and response (EDR) concepts beyond endpoints. While EDR focuses on individual device activity, XDR brings in signals that cross system boundaries (e.g., a compromised laptop accessing cloud storage). This helps teams connect separate events that may be part of the same incident.
What XDR detects
Because XDR consolidates data from multiple sources, it can help track threats as they move across different parts of the infrastructure. Common detection scenarios include:
- Email-to-endpoint attacks: Phishing messages that lead to malware execution or credential theft.
- Credential-based intrusions: Abuse of valid credentials followed by access to cloud or internal services.
- Cross-system malware activity: Threats that move between endpoints and backend infrastructure.
- Multi-stage campaigns: Attacks that progress through several steps over time.
By linking these events together, XDR improves attack surface visibility and helps analysts see how seemingly unrelated alerts connect to a single incident.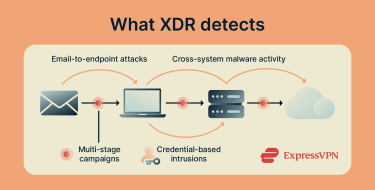
How XDR monitors and correlates data
XDR platforms ingest (and often normalize) telemetry across the environment. Correlation engines then link related alerts into unified incidents, helping teams reconstruct timelines and reduce alert fatigue. This makes it easier to understand timelines, identify root causes, and prioritize response.
Many XDR platforms also support automated incident response. When a platform detects certain patterns, it may trigger predefined actions (often via playbooks), reducing response time during active threats.
Where XDR fits in a security stack
XDR can serve as a central layer for detection and response by bringing investigation and response workflows into a single place. In some environments, it consolidates detections and response actions into one console; in others, it sits above existing controls and connects them through shared incident workflows.
Many XDR platforms extend EDR-style capabilities with integrations across other security domains. As a result, the biggest differentiator is integration depth and coverage: environments with limited integrations or uneven visibility may see less benefit from XDR’s incident correlation and response workflows.
NDR vs. XDR: Key differences explained
Both NDR and XDR improve how organizations detect threats and respond to incidents. The difference is in what they monitor, how they process data, and how easy they are to deploy.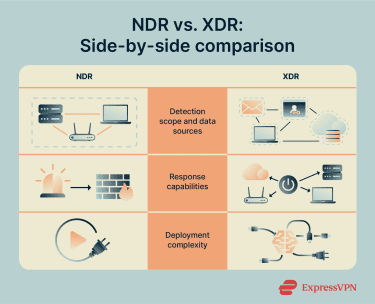
Detection scope and data sources
NDR is optimized for deep visibility into network traffic patterns, making it particularly effective at detecting lateral movement and anomalies within segmented environments. This depth comes from focusing on one domain rather than correlating signals across many
XDR, by contrast, correlates signals from multiple security layers to track attacks that span systems. This broader view can improve cross-stage detection, but its effectiveness depends on how complete and well-integrated those data sources are.
In practice, the trade-off is specialization versus breadth: NDR emphasizes depth in one domain, while XDR prioritizes end-to-end visibility across the attack chain.
Response capabilities
NDR surfaces suspicious activity and adds network context, and the response is often carried out through integrated controls. For example, NDR might flag unusual traffic between a workstation and a database, then trigger containment or traffic-blocking actions via a firewall, network access control (NAC), or endpoint tool, or through a security orchestration, automation, and response (SOAR) platform that coordinates these actions.
XDR platforms coordinate response across multiple systems. When XDR detects a threat, it can automatically isolate an infected endpoint, block a malicious domain, or revoke compromised credentials, reducing response time during active threats.
Deployment complexity
NDR deployments are often simpler to roll out because monitoring is typically agentless. This can reduce rollout friction and help cover assets that can’t run endpoint software, such as IoT devices or printers, though sensor placement and traffic visibility still matter.
XDR usually requires deeper integration across multiple telemetry sources. This increases operational overhead and may introduce vendor lock-in, depending on the platform and its integration openness.
Pros and cons of NDR and XDR
No detection-and-response tool is universally better. NDR and XDR solve different problems, and their strengths and limitations become clearer in the context of real-world environments, operational constraints, and team maturity.
Understanding these trade-offs clarifies what each tool does well and where additional controls may be needed.
Advantages and limitations of NDR
NDR’s strengths come from its narrow focus on network behavior. This provides deep visibility into network activity, but not endpoint-level details such as processes or files.
| Strengths | Limitations | Best fit when. . . |
| Agentless visibility that can reduce rollout friction | Limited native response; relies on EDR/firewall/NAC/SOAR integrations | Environments have many unmanaged assets, like IoT, operational technology (OT), and printers |
| Works with mixed security stacks | Response depth depends on integrations | Adding network visibility without replacing existing tools |
| Strong for lateral movement (east-west) | Limited visibility into on-host details (processes/files/user actions) | Internal movement and segmentation monitoring are priorities |
| Can surface network behaviors that endpoint tools may miss | Less payload insight without decryption | Encrypted traffic is common; metadata-based detections are acceptable |
Advantages and limitations of XDR
XDR’s value lies in correlation and coordinated response across layers, but it depends on strong integrations and consistent telemetry.
| XDR strengths | XDR limitations | Best fit when. . . |
| Cross-domain incident context | Effectiveness depends on telemetry coverage | Visibility is needed across tools/domains |
| Correlated timelines and prioritization | Integration depth varies by vendor | Analysts need faster triage and clearer incidents |
| Coordinated response via automation/playbooks | Higher operational complexity | Response actions should be orchestrated across layers |
| Reduced alert fatigue through correlation | Can be higher cost/overhead (scope-dependent) | Consolidation is preferred over multiple-point tools |
When to use NDR vs. XDR
Choosing between NDR and XDR depends on the environment design and security operations. Factors such as asset diversity, integration tolerance, and response maturity influence which approach delivers the most value.
- Choose NDR: When deep network visibility is the priority, especially for lateral movement and environments with many unmanaged or agentless assets.
- Choose XDR: When incidents regularly span multiple domains and a single workflow for investigation and response is needed, provided integrations and telemetry coverage are strong.
- Use both: In mature or hybrid environments to combine network depth with cross-domain correlation, especially where agent coverage is uneven, and network monitoring remains important for security operations and compliance-driven requirements.
FAQ: Common questions about NDR vs. XDR
Does XDR replace NDR?
No. Extended detection and response (XDR) and network detection and response (NDR) serve different roles in a security stack. XDR correlates telemetry from multiple security layers into incidents, while NDR applies behavioral analytics to network traffic for deep network visibility.
In practice, many organizations use NDR to strengthen internal network visibility alongside XDR’s broader correlation and response workflows, though some XDR platforms include native network sensors that can narrow the gap.
What’s the difference between NDR, XDR, and EDR?
Endpoint detection and response (EDR) monitors activity on individual devices, such as processes, files, and other endpoint telemetry. Network detection and response (NDR) analyzes network traffic to identify suspicious communication patterns. Extended detection and response (XDR) brings together multiple detection sources, often including EDR signals and, depending on the platform, network telemetry, to provide a consolidated view of threats across the environment.
Is NDR suitable for small organizations?
It can be, depending on the environment. Network detection and response (NDR) agentless visibility can reduce rollout friction and help cover unmanaged devices. However, NDR still requires adequate network visibility and ongoing tuning, so many small teams may see the most value when it’s delivered as a managed service rather than operated entirely in-house.
Can XDR reduce alert fatigue?
Yes, when properly configured. By correlating related alerts across domains, extended detection and response (XDR) can reduce duplicate notifications and present incidents in context. The effectiveness depends on the quality and coverage of the telemetry sources feeding the platform.
Are NDR and XDR preventive or detective tools?
Both are primarily detective. They identify suspicious activity and help teams respond more quickly, but they don’t replace preventive controls such as firewalls, access policies, or segmentation strategies.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN