-
What is IoT connectivity, and how do you choose the right solution?
Internet of Things (IoT) devices rely on connectivity to send data to the systems that process it and to receive updates when needed. The quality of that connection affects how reliably a device opera...
-

Types of IP addresses explained: Complete guide
An Internet Protocol (IP) address is a network identifier that tells systems where to send data. Every device that connects to the internet uses one, but not all IP addresses work the same way. Some a...
-

What is DNS cache poisoning? How to detect and prevent attacks
When you visit a website, your device relies on cached Domain Name System (DNS) records to quickly resolve the domain name to an IP address. These cached records are meant to reduce the time needed to...
-

Does a VPN work without Wi-Fi?
A virtual private network (VPN) needs some form of network connection to work, but it doesn’t have to be Wi-Fi. For most people, that means using it over the internet, whether through home broadband...
-
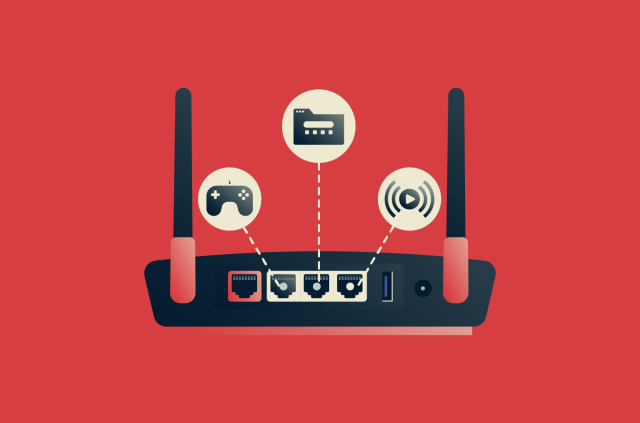
How to open ports on your router
Your router controls how data moves between your home network and the internet. When you open a website, stream a movie, or play an online game, that traffic passes through numbered entry points calle...
-

How to clear Instagram cache on iPhone, Android, and desktop
Instagram can sometimes slow down, with feeds, Stories, or Reels taking longer to load. When this happens, clearing the app’s cache is one of the simplest fixes. This guide explains how to clear Ins...
-

Data sovereignty: What it is and compliance considerations
Every digital interaction generates data. Often, it moves across borders; a login request in Paris might be processed on servers in California and stored in Singapore. Given this constant global excha...
-

What is social engineering? A complete security guide
Not every cyberattack starts with a technical exploit or malicious download. Many begin with seemingly harmless interactions, such as a delivery text, an email from the IT team, or a quick call asking...
-

The ultimate guide to wireless access points
Wi-Fi networks depend on access points to make wireless connections possible. Whether at home, in an office, or across a campus, access points keep your phones, laptops, and smart devices connected an...
-

What is a walled garden?
A walled garden is a digital environment managed by a single tech company, such as Apple or Meta. Within this closed space, the company controls what users can access, how data is shared, and which ap...

This content is not available in your region
To continue, please visit our dedicated website for the United Arab Emirates.
ExpressVPN for UAE
