What is stalkerware, and how to remove it from your phone

Imagine someone secretly watching your every move through your own phone without you even knowing. That’s what stalkerware does.
Most of the time, stalkerware is installed by someone you know—a partner, ex, or even a family member—who wants to monitor or control you. That’s what makes it so dangerous: it’s personal, and it’s hidden.
If you think your phone might have stalkerware on it, don’t panic. This guide will walk you through how to spot the signs and how to remove it. Everyone has the right to feel safe and in control of their device.
What is stalkerware?
Stalkerware is software designed to secretly monitor someone’s digital life. It can run silently on a phone or computer, collecting personal information like messages, call logs, location data, and even audio or video, all without the person ever knowing it’s there.
What sets stalkerware apart is its role in digital surveillance and abuse. It’s often used in controlling relationships, where one person wants to track or dominate another’s actions. This isn’t random cybercrime; it’s targeted, intentional, and deeply personal.
The software itself is often disguised as something harmless or hidden entirely, making it difficult to notice. And because it usually needs to be installed manually, it’s most often placed there by someone with direct access to your device—like a partner or a relative.
How stalkerware works
Instead of flooding the system with pop-ups or alerts like traditional malware might, stalkerware is subtle. It quietly monitors your activity and sends regular updates to the person controlling it, often through a private dashboard or email notifications. They don’t need to keep checking your phone directly; the software does all the spying for them.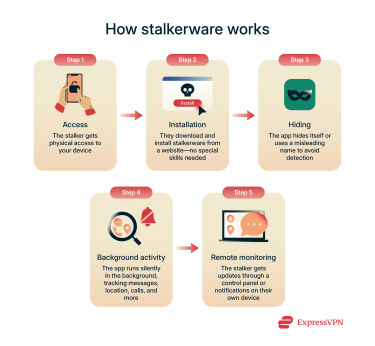
What makes stalkerware different from malware
- It’s personal: Most malware is spread out by anonymous criminals to steal data or make money. Stalkerware, on the other hand, is typically used by someone you know. That personal connection is what makes it feel especially invasive—it’s not just about spying; it’s about control in a relationship.
- How it’s installed: While both stalkerware and malware can be installed through phishing emails, shady links, or suspicious downloads, stalkerware is often installed directly by someone with physical access to your device. A partner, roommate, or family member might only need a few minutes alone with your unlocked phone to set it up.
- Purpose: Malware is built to profit, whether by stealing credit card info or locking your files for ransom. Stalkerware is different. It’s designed to monitor your every move, track who you talk to, and see where you go. It’s about surveillance, not financial gain.
- Hidden in plain sight: Many stalkerware apps look completely harmless, like a calculator, weather app, or system tool. They’re built to avoid detection and won’t show up with suspicious names or behavior.
Is stalkerware legal?
In most cases, no—especially when it’s used to spy on someone without their consent. But the laws can be tricky. In many places, the software itself isn’t illegal; it’s how it’s used that matters. If someone installs it on your device to monitor you secretly, that’s often a serious violation of privacy laws and can even be part of domestic abuse.
Many of these apps are marketed under innocent labels like “parental control” or “employee monitoring,” which creates a legal gray area. But when they’re used to secretly track a partner, ex, or family member, the intent is clearly abusive.
A report by ExpressVPN highlights how stalkerware developers are rarely held accountable—despite violating basic privacy rights. These apps often bypass meaningful consent, and current legislation has limited reach, allowing many to operate freely.
Types of stalkerware and their capabilities
Stalkerware apps don’t always look suspicious. But once they’re on your device, they can give someone an unsettling amount of access to your private life.
These apps come in different forms, each designed to spy in its own way. Some focus on reading your messages, others track your location, and a few dig deep enough to record calls or steal personal files.
- Apps that monitor calls and messages: These let someone read your texts, check your call logs, and, in some cases, even listen in or record your conversations.
- Location tracking software: Using GPS, these apps show exactly where you are—and where you’ve been. They’re often disguised as safety tools for families, but they can be used to monitor you without your knowledge.
- Apps that access your files and photos: Some stalkerware goes even deeper, pulling your photos, videos, and saved files. It can extract sensitive information without leaving a trace.
How is stalkerware installed on devices?
While physical access is the most common method, stalkerware can sometimes be installed remotely, though it’s less typical and usually harder to pull off. These remote methods often rely on tricking the victim into installing the app themselves, without realizing what it really does.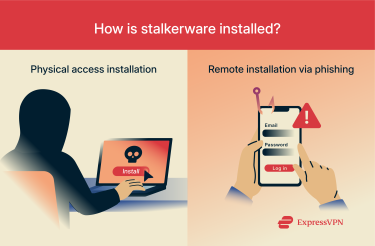
Physical access installation
In most cases, stalkerware is installed by someone who has direct access to your device—and often, just knowing your passcode is enough. The process is quick and simple and doesn't require any advanced skills.
Android devices
On Android, the person installing stalkerware can download the app from a third-party site, grant it the needed permissions, and turn on stealth mode—so it vanishes from the home screen. Once active, it can quietly send out your location, texts, call logs, photos, and even audio or video from your microphone and camera.
iPhones
Apple’s security model makes it difficult to install traditional stalkerware apps, unless the phone is jailbroken, which is risky and leaves clear signs.
Most iPhone surveillance instead happens through iCloud account abuse. If someone has your Apple ID and password (and manages to bypass two-factor authentication), they can log in from another device and view synced data like messages, photos, contacts, and your device location via Find My. No app needs to be installed on your phone for this to happen.
Alternatively, an abuser might give someone an iPhone with stalkerware already pre-installed. Several companies openly offer this as a service, shipping phones with surveillance tools preloaded and hidden, all in factory-sealed packaging. Framed as a gift, the phone seems safe, but it gives the abuser immediate access once the victim starts using it.
Remote installation via phishing or shared links
One common method is phishing: the stalker sends a message with a link that looks legitimate: maybe a fake photo album, app update, or delivery notification. If the victim clicks it and grants permissions, they could unknowingly install stalkerware.
Another approach is disguised apps or file sharing. These might appear as a helpful tool or innocent app (like a game, flashlight, or calendar) but contain hidden and unauthorized tracking functions. In some cases, the abuser sends the app directly through messaging apps or file transfers, making it look like something useful or familiar.
While less common than physical installation, remote methods are still a risk—especially if the stalker is tech-savvy or knows how to manipulate trust.
Signs of stalkerware
Stalkerware is made to stay hidden, but it leaves small traces. You don’t need to be a tech genius—just a few simple checks on your phone’s battery, data, apps, and performance can reveal if something shady is running behind the scenes.
If you suspect someone might be spying on your phone, this guide also outlines several helpful checks you can do to investigate further.
Unusual battery drain, data usage, or background activity
A sudden drop in battery life or a spike in data usage can be one of the earliest warning signs of stalkerware. These apps often run silently in the background, uploading your location, messages, or other personal data to a remote dashboard.
In some cases, your phone may be sending or receiving data when you're not using it, especially during idle hours or overnight. That kind of unexplained background activity can signal that something on your device is transmitting information without your consent.
Unknown apps or configuration profiles
Stalkerware can hide as a normal-looking app or use system-level settings like configuration profiles. Checking these areas is a good way to spot signs of spyware. If you notice anything suspicious, later in this guide, we’ll show you the detailed steps to review and remove them on iOS and Android.
Strange behavior, overheating, or performance issues
If your phone starts crashing, freezing, or showing random pop-ups, it could be a sign that something is interfering with its normal operation. These glitches might seem minor on their own, but if they come along with other red flags, like unknown apps or rapid battery drain, they shouldn’t be ignored.
Stalkerware and similar spyware often run silently in the background and use up system resources, which can lead to sluggish performance or even cause your phone to feel warm when it’s idle. If your device is suddenly laggy, slow to respond, or overheating without a clear reason, it’s worth investigating further.
How to detect and remove stalkerware from Android devices
If you suspect stalkerware is on your phone, it’s important to take care. Trying to remove it or even talking about it might tip off the person who installed it. Consider reaching out to a legal advisor or support organization (such as the National Domestic Violence Hotline) first. They can help you understand your options and stay safe while taking back control of your device.
That said, if you feel safe and ready to move forward—or if you need to act quickly—this guide will walk you through how to remove stalkerware on Android. We’ll also cover iPhones in the next section.
Before taking any action to remove suspicious apps, make sure to save your data, if it’s safe to do so. Take screenshots of suspicious apps, note any unexpected settings changes, and back up your important files. This can help later if you need to show someone what was on your device.
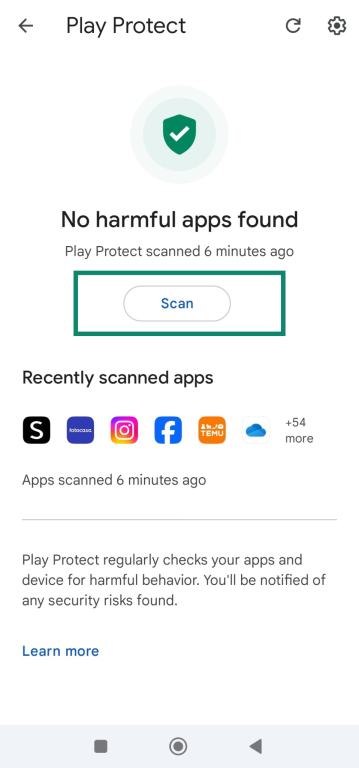
1. Run Google Play Protect
Google’s built‑in Play Protect can find some stalkerware threats.
- Open the Google Play Store app and tap on your profile icon in the top right.
- Click Play Protect (ensure it’s turned on).
- Tap Scan if it’s not already scanning.
2. Use a trusted antivirus tool to detect Android stalkerware
Reputable antivirus or anti-spyware apps can help detect threats that Google Play Protect might miss. These tools can scan your phone for hidden stalkerware and alert you to suspicious activity. Choose one with strong privacy protections and a good reputation for mobile security.
3. Manually check installed apps
Some stalkerware apps won’t appear on your home screen.
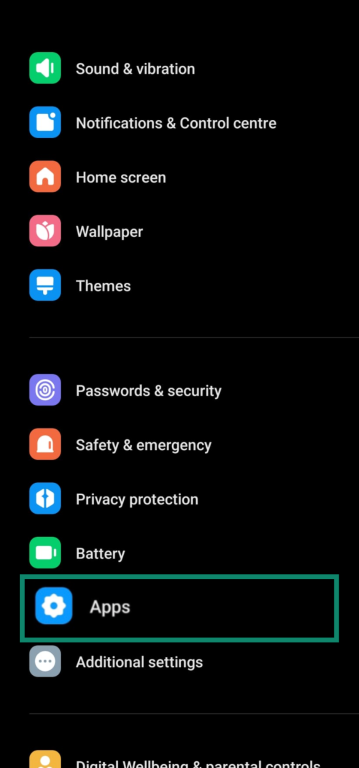
- Go to Settings and tap Apps.
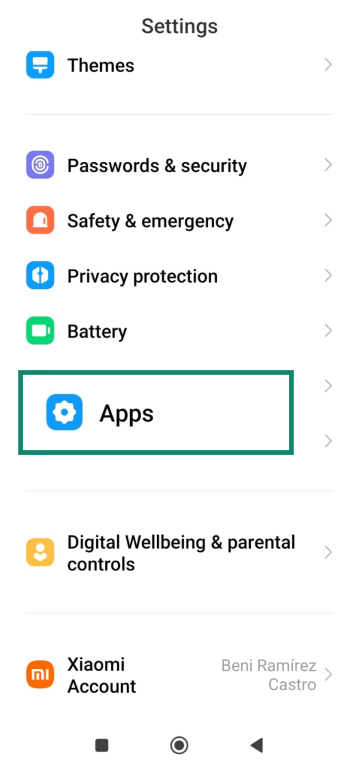
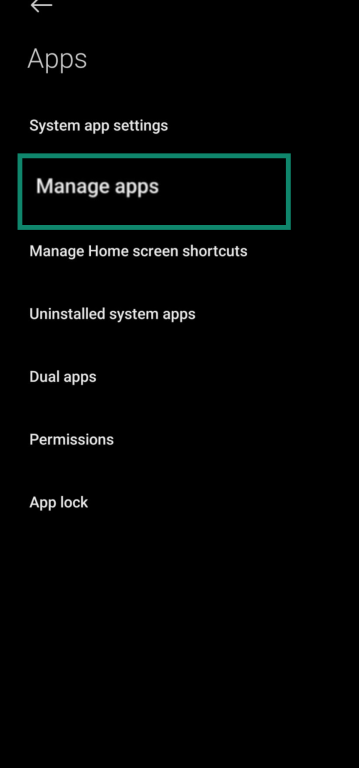
- Click Manage Apps.
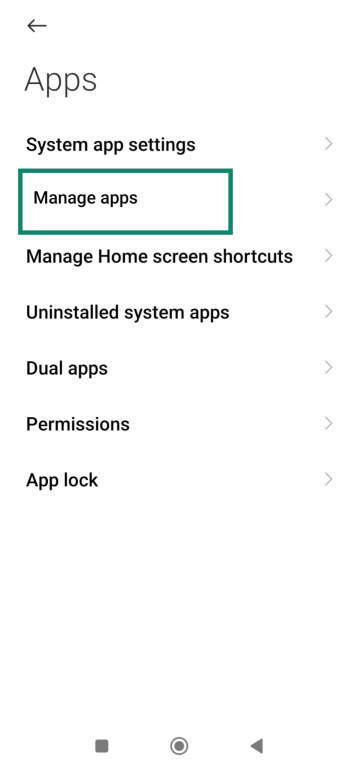
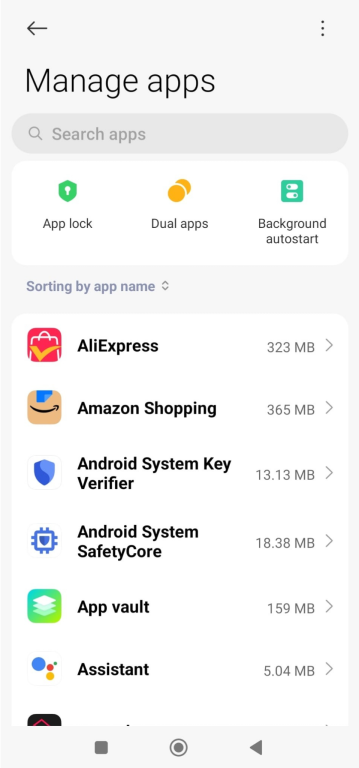
- Scroll through the list and look for apps you don’t recognize or that have generic names like “System Service,” “Device Health,” or “Device Admin.”
4. Check device administrators and accessibility services
Stalkerware can use high-level permissions to avoid detection.
- Go to Settings and tap Privacy Protection.
- Click Other Permissions.
- Go to Device & app notifications.
- If you see apps you don’t recognize or that have generic names like “System Service” or “Device Health,” tap them to review their permissions and disable access if needed.
5. Uninstall suspicious apps
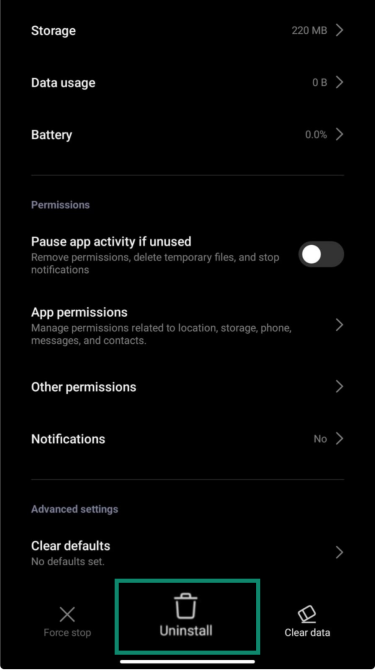
If you spot any suspicious app that you didn't install, it’s best to remove it.
- Go to Settings > Apps.
- Tap Manage apps.
- Tap the app and hit Uninstall.
6. Restart and rescan
Once you’ve uninstalled the suspicious app, restart your device to clear out any lingering background processes. After your phone powers back on, open your antivirus app and run a full scan to make sure the stalkerware has been completely removed.
7. Update your OS and change your passwords
Once you’ve removed the stalkerware, check for any system updates and install them. These updates often fix security issues that could leave your phone vulnerable.
After updating, and only if you’re sure your phone is clean, go ahead and change your passwords. Otherwise, the attacker might intercept your new passwords.
8. Factory reset (if necessary)
If you’re still unsure your phone is clean—or if the app reappears—consider backing up safe files and doing a factory reset. The exact steps may vary slightly depending on your Android version or device, but generally, you’ll need to go to Settings, then System, and look for Reset Options.
From there, tap Erase all data to restore your phone to factory settings and remove anything that might still be hiding.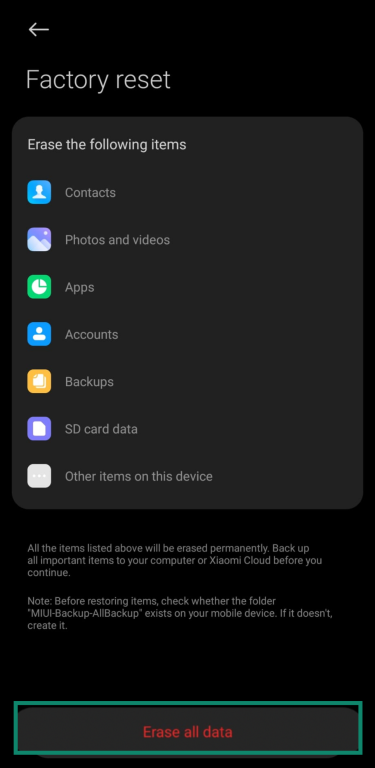
How to detect and remove stalkerware from iOS devices
If you suspect that your iPhone has been compromised by stalkerware, especially if it may have been jailbroken, it’s crucial to act quickly but carefully. This guide walks you through how to detect the signs, remove any threats, and lock down your security.
Step 1. Detect signs of stalkerware or jailbreaking
1. Scan for unfamiliar apps
Some stalkerware apps try to hide but can still appear in your app list.
- Open Settings and go to Apps.
- Check if there are apps you didn’t download yourself or that don’t look familiar.
2. Check for unknown configuration profiles
Suspicious configuration profiles can give third parties deep access to your device.
- Open Settings and go to General.
- Tap VPN & Device Management.
- If you see profiles you didn’t install, tap on them to see the details and consider removing them.
3. Look for jailbreak indicators
Jailbreaking removes Apple’s built-in security protections, which can make your iPhone more vulnerable to stalkerware and other threats. To spot signs of jailbreaking:
- Look for unfamiliar apps like Cydia, Sileo, or Zebra—these are commonly used to manage jailbroken devices and do not appear on standard iPhones.
- Pay attention to unusual phone behavior, such as frequent crashes, unexpected pop-ups, or apps that suddenly have new features or permissions.
- Notice if your phone allows actions Apple normally blocks, like making deep customizations to the interface.
Step 2. Remove stalkerware and restore security
The safest way to restore your security is to reset your device to factory settings. This process will erase all your data, remove any unauthorized apps or changes, and return your iPhone to its original state.
1. Back up your data
Before you reset your phone, make sure to back up your important information so you don’t lose anything you need.
- Go to Settings and tap on your Apple ID at the top of the screen.
- Select iCloud.
- Tap iCloud Backup.
- Click Back Up Now to start the process.
2. Erase your iPhone
Once your data is safely backed up, you can erase your iPhone:
- Go to Settings and tap General.
- Select Transfer or Reset iPhone.
- Choose Erase All Content and Settings and follow the on-screen instructions to complete the reset.
This will completely erase your phone’s data, remove any stalkerware, and undo any jailbreak-related changes. After the reset, you can restore your data from your iCloud backup during the setup process.
Step 3. Lock down your Apple account
Strengthening the security of your iCloud account is key to keeping your personal data safe from unauthorized access. Apple offers several options to help protect your account and everything you store in iCloud:
- Turn on two-factor authentication (2FA): This is a must-have security feature that adds an extra step when you sign in. Even if someone guesses your password, they won’t get in without a special code sent to your trusted devices. It’s like having a second lock on your door.
- Enable Advanced Data Protection: This feature encrypts almost everything in your iCloud — from your backups to photos and notes — so only your trusted devices can unlock it. It’s peace of mind knowing your data stays private.
- Check your connected devices: Take a moment to look at all the devices linked to your Apple account. If you see any that you don’t recognize or no longer use, remove them. This helps stop anyone else from accessing your info through a forgotten device.
- Use strong, unique passwords: Make sure your Apple ID password is tough to guess and different from other passwords you use. And don’t share it with anyone.
How to protect yourself from stalkerware
Protecting yourself from stalkerware is about making your phone and data harder for someone else to access. These simple steps can help reduce your risk and keep your information more secure:
Use strong screen locks and 2FA
Setting up a strong screen lock, like a password, PIN, or biometric option such as fingerprint or facial recognition, can help stop someone from getting into your phone if they pick it up.
Turning on two-factor authentication for your online accounts adds another layer of security. With 2FA, even if someone manages to get your password, they won’t be able to log in without an extra code that’s sent to you or generated on your phone.
Keep OS and apps updated
Keeping your phone’s operating system and apps updated is a good way to close security gaps. Updates often include fixes for vulnerabilities that could let someone install stalkerware on your device. If you see a new update, install it as soon as possible.
It can help stop stalkerware from finding ways to hide on your phone or use old security holes. Regular updates can also make your phone run better overall and keep it safer from other types of digital threats.
Limit device access and permissions
One way to make your phone safer is to keep a close eye on what apps you install and what permissions they have. Apps that can see your location, camera, or microphone can be risky if you don’t trust them.
Go through the permissions on your device and remove anything that doesn’t make sense or that you don’t need. This can help block stalkerware from using those permissions to track or record you.
Install trusted security tools
One of the most effective tools for better online protection is a VPN. While a VPN won’t directly detect stalkerware, it can help protect your online activity from being monitored, especially if someone is trying to snoop through the same Wi-Fi network.
A trusted VPN like ExpressVPN encrypts your internet traffic and hides your IP address, making it much harder for someone to intercept your data or track your browsing habits. ExpressVPN has also undergone independent security audits to verify the safety and integrity of its apps.
To strengthen your defenses, you can also use mobile security tools that scan for spyware or suspicious apps. Some offer breach alerts or guidance to help you adjust your device settings for better privacy. Using both a VPN and antivirus software can give you broader protection against different types of threats.
Learn more: For broader protection tips, check out this mobile device security guide covering best practices to keep your device safe.
FAQ: Common questions about stalkerware
Are stalkerware apps legal in my country?
Installing stalkerware on someone else’s device without their consent and covert monitoring are illegal in most countries. While some of these apps might be marketed as “parental control” or “employee monitoring” tools, using them without someone’s knowledge can break laws and put you at risk of legal trouble.
Can an antivirus detect stalkerware?
Yes, many antivirus apps can detect a privacy invasion such as stalkerware, especially if it’s known spyware. However, some stalkerware programs might be hidden or disguised to avoid detection. Running a security scan regularly is a good way to catch anything suspicious.
Can stalkerware be installed remotely?
It depends on the app. Most stalkerware needs physical access to your phone for installation, but there are some cases where a stalker might use phishing links or malicious downloads to try to get it onto your device. That’s why it’s always important to be careful about what you click on and download.
Who typically uses stalkerware apps?
Stalkerware is often used by people trying to control or watch someone without their knowledge. This can include abusive partners, family members, or even employers. These apps give them access to private messages, location data, and other personal details, which can be a form of digital abuse.
What should I do if I suspect my partner is using stalkerware?
If you think your partner might have installed stalkerware on your phone, focus on your safety first. Don’t try to remove the app right away if you think it might put you at risk. Instead, look for help from trusted friends or groups that support victims of digital abuse. Remove stalkerware right away only if you think it’s the right move.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN







Comments
If you switch to the router possibility for up to five devices what if any might be drawbacks re speed or any other
I thought your app stopped ads, etc from my browsing showing up on my phone?
While a VPN can shield your traffic from third parties and increase your privacy, there are many scenarios in which your browsing can be tracked by companies. For example, if you use Facebook or Google, they can see your activity during your session and serve you related ads. We recommend using DuckDuckGo as your search engine, along with a browser that can be customized to give you maximum privacy. https://www.expressvpn.com/blog/browsers-block-third-party-cookies/
Can you please list all the items that vpn express doesn’t block / cover, and what settings imperative to have switched on?